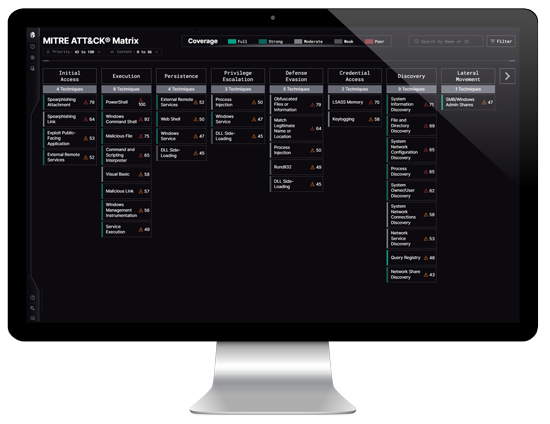
-
Campaign Readiness Guide for Advisory: Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475
Read MoreRecently U.S. Agencies released a Joint Cybersecurity Advisory (CSA), Multi Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475.

-
CISA adds Citrix ShareFile flaw to the KEV catalog
Read MoreLockdown Mode ‘is the best defense that we have today for Pegasus and Predator,’ the notorious, zero-click Android and iOS spyware, Runa Sandvik tells security pros at Mitre Corp.’s ATT&CKcon.

-
Interpres Named to the Enterprise Security Tech 2023 Cyber Top 20 Awards List
Read NewsWe are very excited to announce that Enterprise Security Tech named Interpres Security to its 2023 Cyber Top 20 awards list!

-
TechTarget: Security hygiene and posture management: A work in progress
Read MoreSecurity hygiene and posture management may be the bedrock of cybersecurity, but new research shows it is still decentralized and complex in most organizations.

-
Cybersecurity is: Competition – Here’s the Playbook – Part 3
Read BlogTo successfully resolve any conflict, or win a competition, there are three things you must do: You have to successfully plan, bring capabilities to bear, and keep score. Let’s explore this in more detail with a generic sports metaphor.

-
Cybersecurity Is: Expensive … And It’s Your Fault – Part 2
Read Blog“Cybersecurity is expensive and it’s your fault” seeped into my conscious while I was sleeping, and I awoke a little rattled.”

-
Defense Surface Management is the Missing Link to your CTEM Program
In 2015, officials from the DoD and NSA asked one simple question that served as the catalyst for Threat-Informed Defense (TID) and Continuous Threat Exposure Management (CTEM): “Are we managing...Read Blog
-
Campaign Readiness Guide for Advisory: People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection
Recently, the U.S. and International Agencies release a Joint Cybersecurity Advisory (JCA) (People's Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection | CISA) regarding VOLT...Read More
-
Cybersecurity Is: Failing… How do we start to Win? – Part 1
Read BlogCybersecurity is failing but this shouldn’t be news to you.

Interpres Security operationalizes TTP-based threat intelligence and automates continuous exposure monitoring to help CISOs and security practitioners reduce threat exposure. The Interpres Threat Exposure Management Platform analyzes the dynamic relationship between defensive and adversarial capabilities, assets, and their exploitable vulnerabilities; prioritizes the required defensive actions; and optimizes the security environment, to provide continuous threat exposure management.