This is Part 1 of our "Cybersecurity Is" Series.
After reading this entry, consider finishing the series with:
Cybersecurity Is: Expensive … And It’s Your Fault – Part 2 and Cybersecurity is Competition – Here’s the Playbook – Part 3.

Consider the Following:
There are a lot of solutions floating around to try to solve these problems – new compliance and regulatory frameworks, strategies, capabilities, concepts – but the one thing I have not seen, and I believe can help make a difference is going back to the fundamentals of leadership – namely establishing Unity of Effort.
Over the course of my federal service, I’ve been extremely fortunate to be in the presence of some of the best leaders in the world – and I have had the opportunity to study leadership at one of the finest institutions in the world to make leaders. Each leader, through words and deeds, established Unity of Effort.
Unity of Effort is about getting everyone on the same page about an objective. One of the four stars that I worked for told me once that he repeats his message 20x time a day. He is singular focused on ensuring that everyone understands what we are trying to do, why we are trying to do it, and the risks if we fail.
Cybersecurity has had a difficult time articulating unity of effort. The reasons are simple, we’ve stopped talking about outcomes and instead focused on efforts. We offload risk – cyber insurance or the bank will take care of it. 20 years ago, we argued that “Open-source software would be more secure, since everyone could review the code” but now we have a software supply chain issue. Bad guys use vulnerabilities; therefore, the developers must not think about security. We are not getting support from the Board of Directors, put a cyber savvy person on the board! Continuously focusing on effects as opposed to outcomes.
Moving from effects to outcomes – establishing Unity of Effort.
First, a couple of things – what are the benefits of establishing unity of effort.

Step 1: Establish Unity of Effort – A leader must articulate a concrete objective- which can be measured. Consider the following two statements:
Which of these two things would your rather do? Protect the data? Or Deny and Degrade the adversary? So, if we are going to establish Unity of Effort across the organization, we need to provide clarity on the objective.
Step 2: Deconstruct the Objective into relatable terms:
For an example, let’s break down how ransomware gangs leverage Emotet:
Step 3: Deny and Degrade
Step 4: Building the Message
Now that we have an objective, we can start to build unity across the organization, vertically and horizontally. A messaging campaign that clearly states, who, what, why and what we are going to do, as well as shortfalls should be included.
Step 5: Tailor the Message
Step 6: Build a Security Culture
Once you have an articulated concrete objective, it’s time to build a culture of security. The easiest way is to celebrate wins. If an employee flags an email and says it’s suspicious- Celebrate! Send them Card! Make a bulletin board! Be creative – we all know people like to be rewarded. If the IT staff pre-coordinates a network change, and wants to know if it’ll impact something import, send a note to their Supervisor thanking them. Do the little things of rewarding.
In the event, the opposite happens, make it a learning experience, not a punitive experience.
In summary: Build Unity of Effort, Build a strong team, let’s get after the bad guys and start winning.

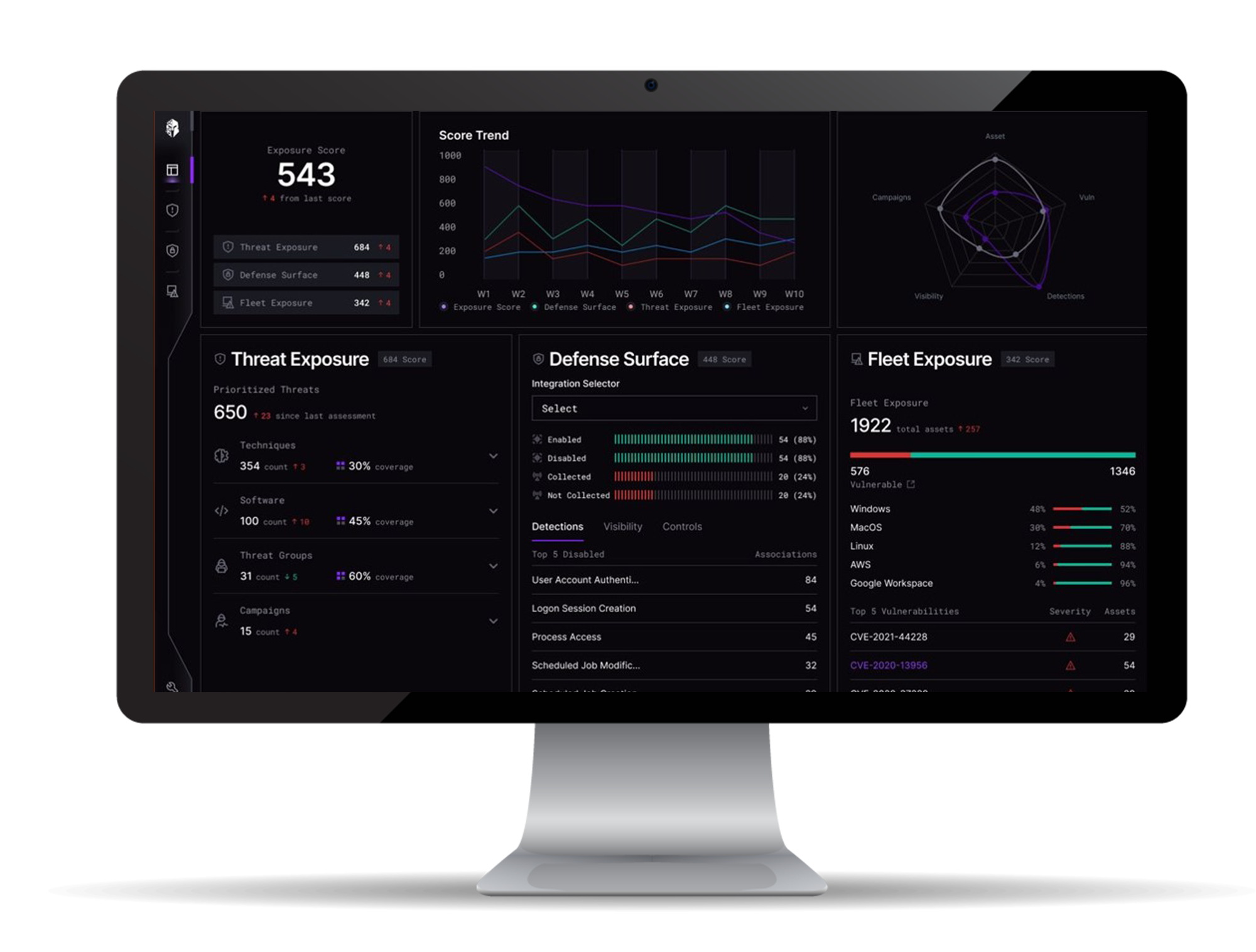
Interpres right-sizes your defensive strategy against the cyber threats that matter most. Our automated, evidence-based platform analyzes the dynamic relationship between your defensive capabilities and adversarial threats, prioritizes recommended actions and optimizes your security ecosystem. We provide an unbiased view of your security posture and continuously measure threat exposure so you can focus resources on the most relevant threats.
i Gartner Predicts Nearly Half of Cybersecurity Leaders Will Change Jobs by 2025
ii In the same article, 92% increased their budget for IT Well-funded security systems fail to prevent cyberattacks in US and Europe: Report | CSO Online
iii The cybersecurity industry is short 3.4 million workers—that’s good news for cyber wages | Fortune
iv Why stock prices often rise after a data breach – IT Governance USA Blog