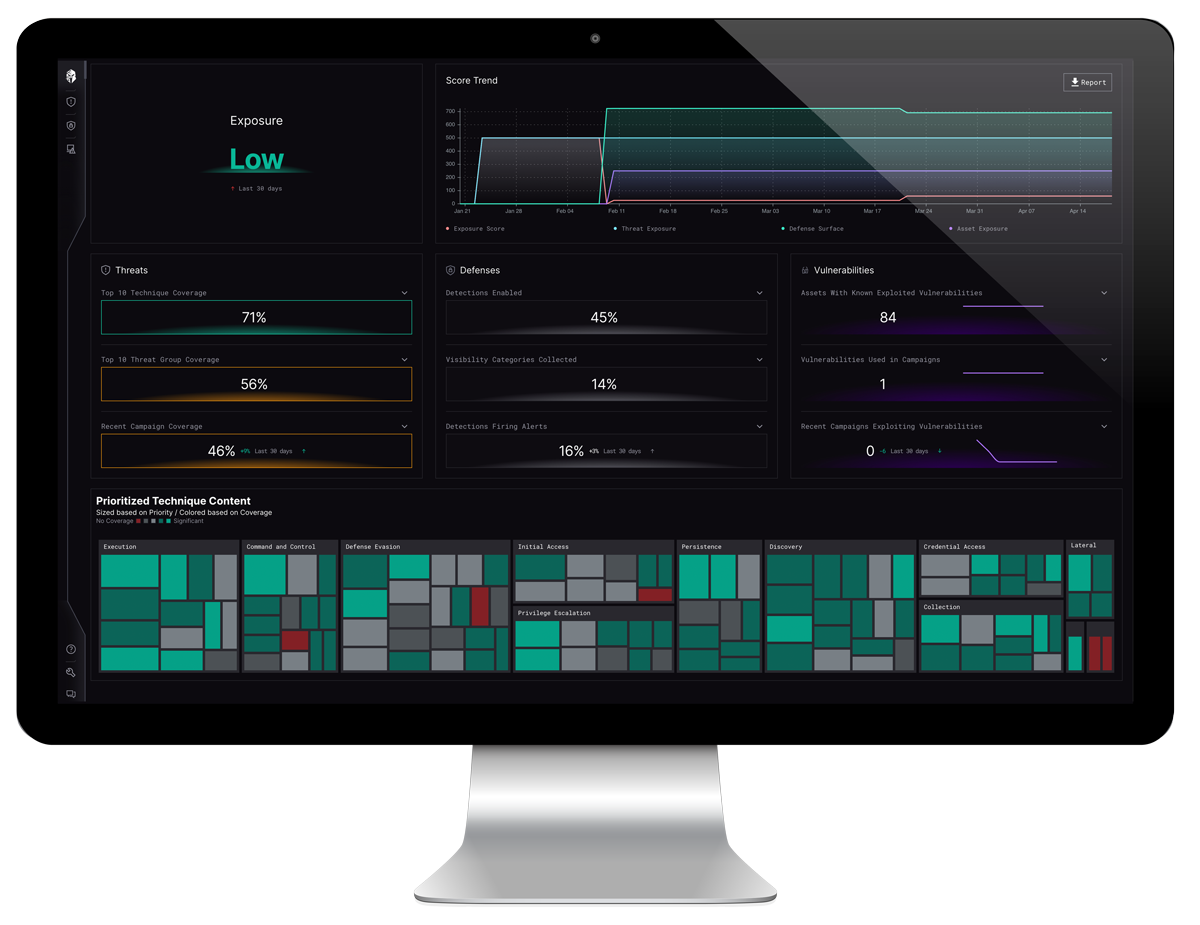
Interpres Security operationalizes TTP-based threat intelligence and automates continuous exposure monitoring to help CISOs and security practitioners reduce threat exposure. The Interpres Threat Exposure Management Platform analyzes the dynamic relationship between defensive and adversarial capabilities, assets, and their exploitable vulnerabilities; prioritizes the required defensive actions; and optimizes the security environment, to provide continuous threat exposure management.

Prioritize Vulnerability & Patch Management Through Continuous Threat Exposure Management
Leverage Vulnerability Intelligence to Reduce Risk Faster
- Identify high-impact vulnerabilities and their associated assets.
- Save time remediating vulnerabilities you cannot fix.
- Monitor the relationships between critical assets, defense surface and exploitable vulnerabilities.
- Focus efforts against vulnerabilities most-likely to be exploited.


Prioritize Vulnerabilities Through the Lens of ‘Threat’
- Know what common vulnerabilities and exploits (CVEs) pose the greatest risk
- Prioritize CVEs adversaries are targeting.
- Remediate vulnerabilities that your adversaries prefer.
- Apply TTP-based threat intelligence to your vulnerability management solutions to achieve speed and scale across your patching program.
Continuously Monitor Assets, Vulnerabilities, and Defensive Controls
- Validate your ability to mitigate based on detection coverage and visibility of vulnerabilities susceptible to exploit.
- Leverage a real-time situational feed of your cyber eco-system that exposes hidden weaknesses in your patching program.

Automate and align your vulnerability management program with threat-informed vulnerability intelligence
Know what exploitable vulnerabilities are being used to target you
Identify which vulnerabilities are important to patch because they’re being used by adversaries targeting organizations like yours
Know what assets have vulnerabilities associated with active adversarial campaigns
Determine the impact a campaign could have on your organization
Know what vulnerabilities should be prioritized and patched first
Save time to prioritize and focus resources on what to patch first
Know if your defense surface is prepared to mitigate exploitable vulnerabilities
Validate your detection coverage and visibility on vulnerabilities susceptible to exploit.