Interpres Security operationalizes TTP-based threat intelligence and automates continuous exposure monitoring to help CISOs and security practitioners reduce threat exposure. The Interpres Threat Exposure Management Platform analyzes the dynamic relationship between defensive and adversarial capabilities, assets, and their exploitable vulnerabilities; prioritizes the required defensive actions; and optimizes the security environment, to provide continuous threat exposure management.
Close Menu
- Platform
- Solutions
- Use Cases
- Understand Cyber Defense ReadinessAssess and validate your cyber defense readiness.
- Optimize Your Defense SurfaceAccurately measure and tailor your security defenses.
- Prioritize Exploitable VulnerabilitiesPrioritize exploitable vulnerabilites & patch management.
- Automate Holistic MITRE ATT&CK® AnalysisMap to MITRE & evaluate detection capabilities against adversarial threats.
- Solutions For
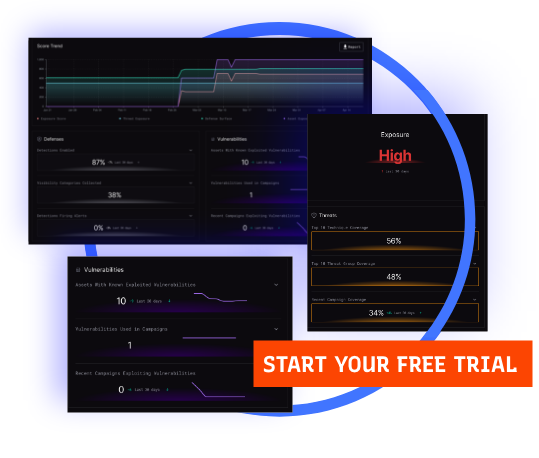 Understand Your Top Threats & Vulnerabilities, TodayTry the Interpres Threat Exposure Management Platform for FREE for 30 Days.
Understand Your Top Threats & Vulnerabilities, TodayTry the Interpres Threat Exposure Management Platform for FREE for 30 Days.
- Use Cases
- Resources
- Company
- Who We Are
 About InterpresLearn more about the Interpres Security Team and our founding story.
About InterpresLearn more about the Interpres Security Team and our founding story. LeadershipGet to know our Leadership team and our Advisory Group.
LeadershipGet to know our Leadership team and our Advisory Group. NewsroomStay up to date on the latest announcements and news.
NewsroomStay up to date on the latest announcements and news. Compliance and CertificationsWe’re dedicated to ensuring our technology adheres to industry compliance requirements.
Compliance and CertificationsWe’re dedicated to ensuring our technology adheres to industry compliance requirements.
- Connect With Us
 PartnersBecome an Interpres partner to help customers address security challenges and grow your business.
PartnersBecome an Interpres partner to help customers address security challenges and grow your business. CareersExplore current career opportunities and join the Interpres team.
CareersExplore current career opportunities and join the Interpres team. Contact UsNeed to get in touch with support or sales? Contact us and let us know how we can help.
Contact UsNeed to get in touch with support or sales? Contact us and let us know how we can help. EventsJoin us for a live event near you.
EventsJoin us for a live event near you.
 Foundations for Continuous Threat Exposure Management: Implementing a Threat-Informed Defense Strategy
Foundations for Continuous Threat Exposure Management: Implementing a Threat-Informed Defense Strategy
- Who We Are
- Request a Demo
- Request a Free Trial








