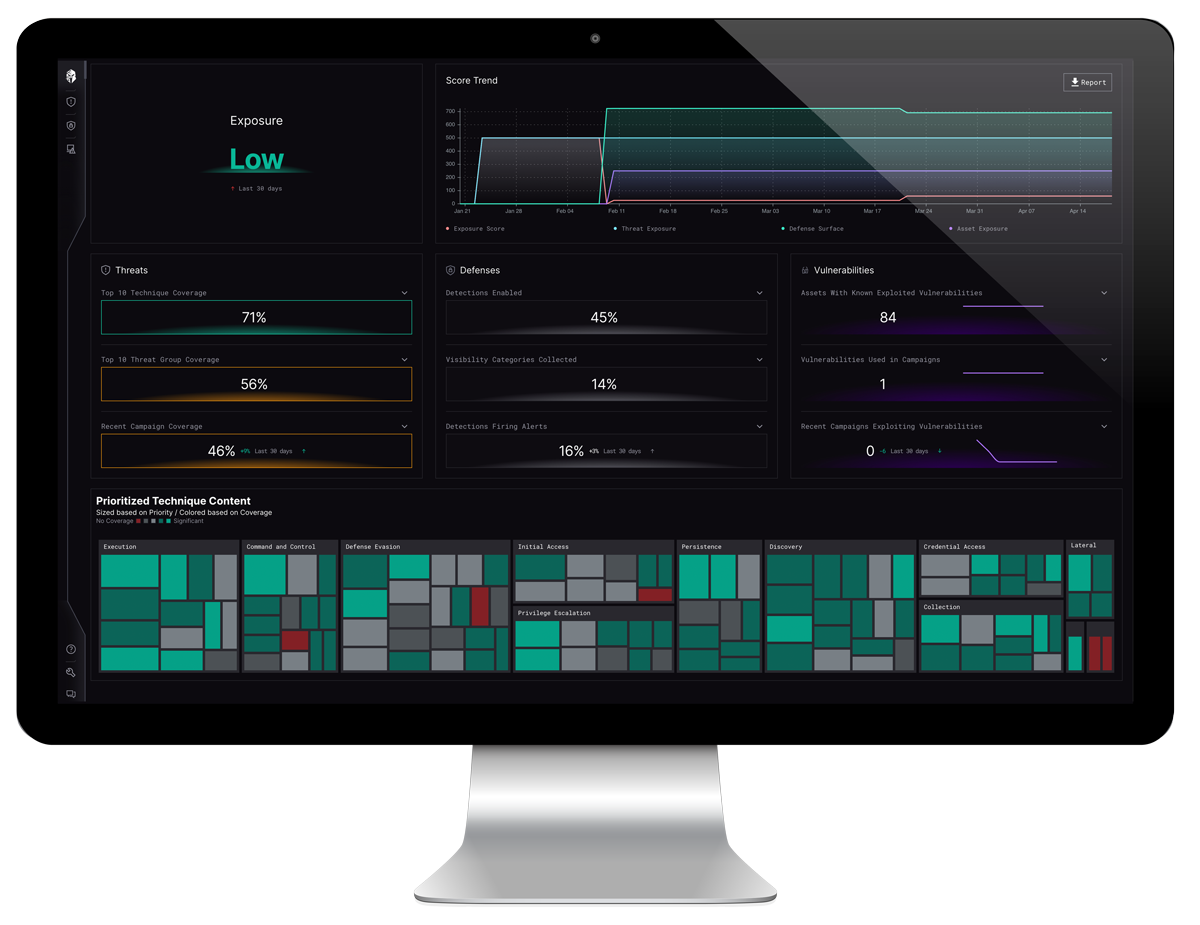
Cybersecurity is a constant uphill battle. Threats evolve faster than defenses, leaving organizations scrambling to catch up. Gartner predicts that by 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.
The proof is in the pudding. Organizations who proactively rethink how they are defending their networks and consistently garner contextual understanding of threat campaigns that are actively targeting their organizations will always be ahead. Make no mistake, cybersecurity is a constant battle of adapt or die, and those who remain one step ahead of their adversaries will continue to thrive.
This is where Interpres Security steps in, armed with a new threat-informed approach: mapping adversarial techniques, tactics, and procedures (TTPs) to your specific security stack. But how does this work, and why is it a game-changer?
We focus on helping organizations optimize their defense surface, to ensure their security measures are tailored to the actual threats they face. To effectively optimize your cyber defenses requires knowing the strengths and weaknesses of your security program. You can’t accurately measure your security defenses without mapping to threats – Adversarial TTPs that you are most likely to encounter.
The Intelligence Advantage
Many senior leaders in the cybersecurity sector have claimed that nobody truly knows how to operationalize threat intelligence, with some even claiming that you should not use it at all. At Interpres, we wholeheartedly disagree. Defining the operationalization of threat intelligence varies from organization to organization, depending on how you derive a course of action based on traffic entering your network.
Organizations with limited resources often struggle with this charge, left clueless if an alert is even something they should be concerned about, likely because they are relying on generic threat feeds. Interpres doesn’t rely on generic threat feeds. The Interpres Threat Exposure Management Platform ingests TTP-based intelligence from over 30 sources including robust national intelligence such as Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and MITRE.
Over the years, the cyber defense industry has amassed a wealth of TTPs that have been made widely available by organizations such as the...
The use of this intelligence dives deep into how real attackers operate, providing an understanding of their preferred tools, techniques, and targets.
From Intelligence to Insight
Interpres doesn’t stop at data collection. It fuses this intelligence with your unique security environment. This involves:
Mapping TTPs to your vulnerabilities:
By analyzing your specific systems and configurations, Interpres identifies how likely adversaries are to exploit your weaknesses.
Assessing your defensive capabilities:
Interpres takes a deep dive into your security tools and protocols, gauging their effectiveness against specific TTPs.
The Threat Landscape Revealed
With this analysis, Interpres paints a clear picture of your threat landscape. You not only see the most likely threats targeting your organization, but also the most dangerous attacks you might face. This empowers you to:
Prioritize defenses:
Focus resources on mitigating the attacks most likely to impact your organization.
Identify gaps in your armor:
Patch vulnerabilities that align with high-risk TTPs, closing critical security holes.
Prepare for the worst:
While unlikely, be ready for sophisticated attacks by understanding how they might exploit your defenses.
Security teams are in a constant state of exhaustion, and with hundreds of thousands of alerts being brought to their attention every day, it is easy to see why. The industry has been longing for a solution that will simply tell them what threats and vulnerabilities are the most critical, allowing organizations to shore up their defenses against the threats that matter most.
Consider this: If you want to defend Planet Earth from an attack of the Martians, and you know there are two groups of Martians in space planning to launch attacks in a direction, wouldn’t you like to know what direction the Martians are planning on attacking?
The same parallel exists in security, and with Interpres, you can know exactly who your adversary is, what they are planning on using for their attack, as well as where they are planning on attacking you.
The Interpres Difference
At the end of the day, the simple truth is that Interpres goes beyond traditional security solutions. Through offering quantifiable data, Interpres allows organizations to move beyond guess work with irrefutable hard data on your threat exposure and the effectiveness of your defenses.
With continuous monitoring, Interpres allows you to stay ahead of the curve with constantly updated threat intelligence and ongoing analysis.
Lastly, with actionable insights, Interpres provides you with clear recommendations on how to improve detection capabilities and optimize your security posture based on the threats that are actually targeting you.
In the cybersecurity arms race, knowledge is power. Leveraging TTP-based threat intelligence and mapping it to your environment with Interpres empowers you to keep your friends (defenses) close and your enemies closer. By embracing the TTP-powered approach that Interpres offers, you can finally gain the upper hand by customizing defenses to combat the greatest risks to your organization.
Ready to See How You Can Start Optimizing Your Defense Surface?
Interpres is dedicated to helping companies just like yours optimize security performance with an unbiased view of your security capabilities, so you can:
Automate your threat intelligence analysis and operationalize TTP-based threat intelligence.
Quickly identify and remediate threats and exploitable vulnerabilities likely targeting your organization.
Determine your level of cyber defense readiness against your set of prioritized threats.
Learn how to Accurately Measure and Tailor Your Security Defenses.