-
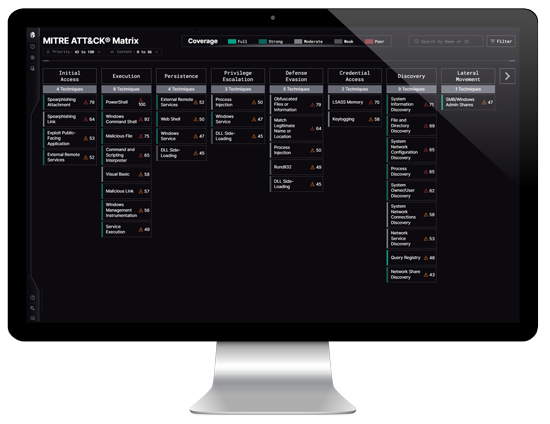
Maximizing MITRE ATT&CK: Enhancing Threat Exposure Management with Interpres Security
Read BlogMaximizing MITRE ATT&CK for comprehensive threat exposure measurement requires a holistic approach that integrates auto-mapping detection analysis, proper security log collection, effective security tooling, and operationalizing threat intelligence from an asset and vulnerability perspective.

-
Techspective: Interpres Security Unveils Major Platform Updates to Combat Cyber Threats
Read MoreHear From Industry Experts – This year’s World Backup Day, which falls on March 31st, 2024, is a prime opportunity to re-evaluate your backup strategy…

-
Threat Exposure Management: Prioritizing Threats for Strategic Defense
Read MoreIn this SANS First Look virtual event, we look at Interpres Security – a platform built to help organizations examine their current security posture and how they compare against the latest threats and vulnerabilities…

-
Cyber Defense Readiness Assessment: Interpres Workflow Demo
Read MoreDetermine your cyber defense readiness within minutes, not days. See a demo of the Interpres Readiness Assessment Platform Workflow.

-
Understanding Cyber Defense Readiness with Interpres Security
Read MoreCo-Founders of Interpres Security discuss the origin story around the Interpres Threat Exposure Management technology and the central problem it solves for — Cyber Defense Readiness.

-
Join Interpres Security in San Francisco for RSA, BSides, the ISSA Cyber Executive Forum & Other Events
Read MoreHead of Threat Research at Interpres hosts session at BSides San Francisco on using AI as an “intern” for continuous threat intelligence.

-
Threat Exposure Management: Introducing Interpres Security
Read MoreGet a glimpse of the problems Interpres Security solves and capabilities that deliver speed and scale to the threat analysis and exposure management.

-
Product Overview: Interpres Threat Exposure Management Platform
Read MoreHear from Co-Founder and Head of Product Management Ian Roth about Interpres tech innovation arms organizations with the insights and capabilities necessary to fortify their cybersecurity defenses and stay ahead of the evolving threat landscape.

-
New Capabilities to Mitigate Threat Exposure and to Continuously Validate Cybersecurity Defenses: Q2 2024 Product Update
Read BlogInterpres releases major platform updates at RSA 2024, adding new capabilities for improved threat exposure management.

Interpres Security operationalizes TTP-based threat intelligence and automates continuous exposure monitoring to help CISOs and security practitioners reduce threat exposure. The Interpres Threat Exposure Management Platform analyzes the dynamic relationship between defensive and adversarial capabilities, assets, and their exploitable vulnerabilities; prioritizes the required defensive actions; and optimizes the security environment, to provide continuous threat exposure management.