Within the cybersecurity industry, we are told all too often that the threat landscape is ever-changing and protecting your organization against the most critical vulnerabilities and threats is paramount. For years, CISOs and cybersecurity practitioners have tried to defend against ALL threats facing their organizations, buying product after product, and spending millions of dollars on solutions that they *think* will work. In fact, the average organization has 70+ tools in their security stack that they must manage, integrate, and configure properly to get the maximum benefits. However, adversaries only exploit 2-7% of known CVE’s, taking advantage of unpatched/unmitigated systems, and security control entropy. Security teams are executing a strategy that is misaligned with the actual threats and targeted vulnerabilities. Simply put, this generalized, “one-size-fits-all” approach has failed.
On top of that, CISOs struggle to quantify risk and report on risk posture to their Boards of Directors. Gartner predicts that by 2025, 50% of cybersecurity leaders will have tried, unsuccessfully, to use cyber risk to drive enterprise decision making.
Taking all of this into account, enterprises need a new strategy when it comes to their security defenses. This “defend everything” mentality is not realistic, and it doesn’t work. CISOs and security teams must effectively prioritize and defend against the threats that matter most, based on their unique threat profile. The question is: Where do you start? The answer: Defense Surface Management (DSM).
DSM and its link to Threat-Informed Defense & Exposure Management
As a concept, Defense Surface Management right-sizes your defensive strategy against the cyber threats that matter most. It analyzes the dynamic relationship between your defensive capabilities and adversarial threats, prioritizes recommended actions, and optimizes your security ecosystem. It provides an unbiased view of an organization’s security posture and continuously measures threat exposure to focus limited security resources on the most relevant threats.
With the specificity of cyber attacks we see today, protecting against every possible attack path is impossible and unsustainable. To combat this challenge, many organizations have turned to threat-informed defense (TID) – a proactive approach emphasizing the understanding of adversary motives and how to effectively defend against them.
Other organizations are turning towards Continuous Threat Exposure Management (CTEM) to continuously evaluate the exploitability of digital and physical assets.
What has been ignored for years is the gap between those two schools of thought, and the need for defense surface management. Rather than viewing these concepts as flat and equal, we have to adopt the mindset that threat-informed defense is the baseline for automated Defense Surface Management, which serves as the enabling capability for true exposure management.
In the past, Defense Surface Management has been a manually intensive process, resulting in significant security engineering, spreadsheet analysis and general frustration. Defense Surface Management drives the need for an automated, evidence-based platform to analyze, prioritize, and optimize the security ecosystem for each enterprise’s unique security posture.
Key Criteria for Evaluating DSM Solutions
In examining your options for Defense Surface Management and threat exposure management solutions, you must keep a checklist of the things that will matter most to your organization. The ideal Defense Surface Management will provide:
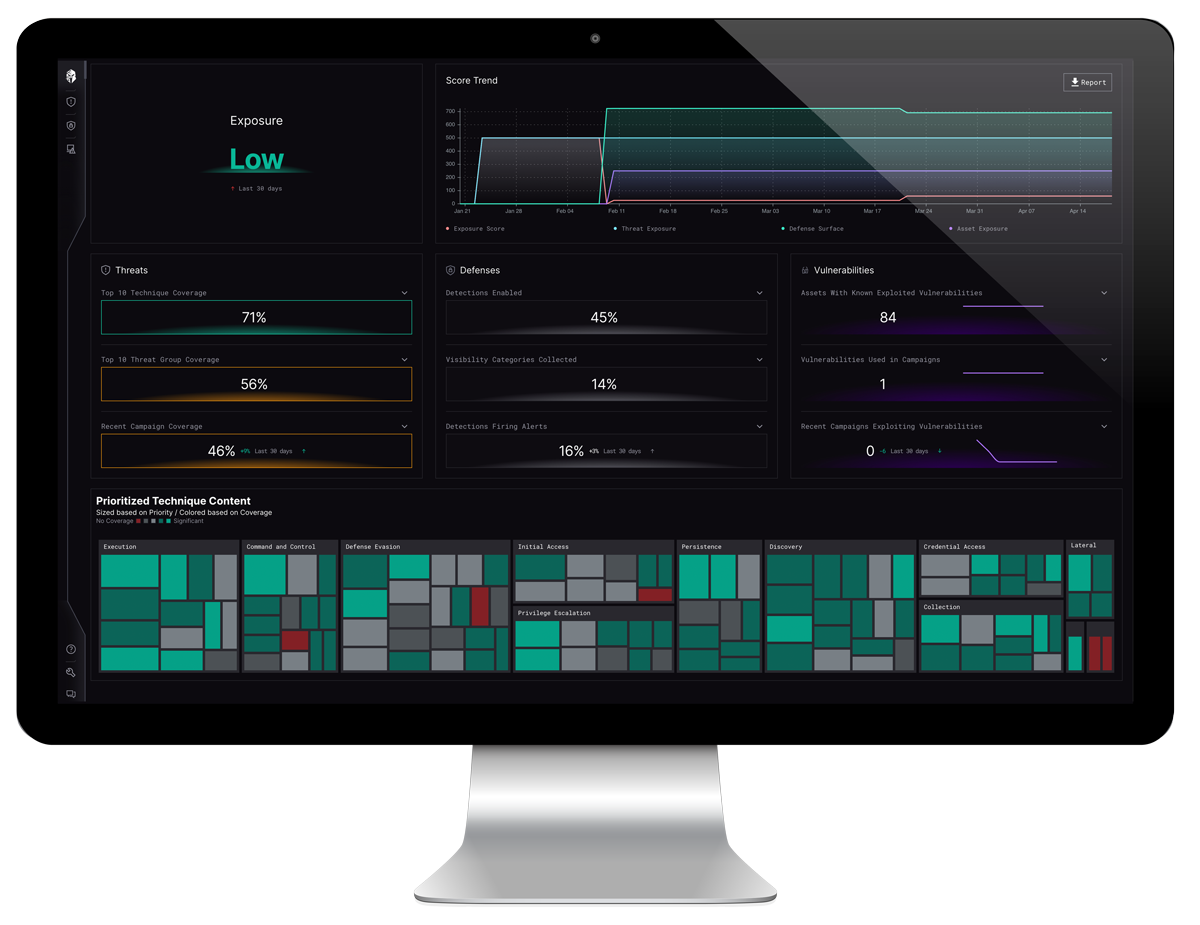
Automating this due diligence checklist, Interpres now offers the Interpres Exposure Index as part of its patented, multi-tenant SaaS offering, the Interpres Defense Surface Management Platform. By scoring an organization’s threat exposure, defensive posture, and asset exposure, the Exposure Index provides a precise view of an organization’s threat posture.
To better understand exactly how the Interpres Defense Surface Management platform can work for you, be one of the first 50 to sign up here to receive a free demo.
For more information on how Interpres Security is providing unbiased, agentless, and sensorless advice on your environment and for a true examination of what’s working and where your inefficiencies are, visit www.interpressecurity.com.