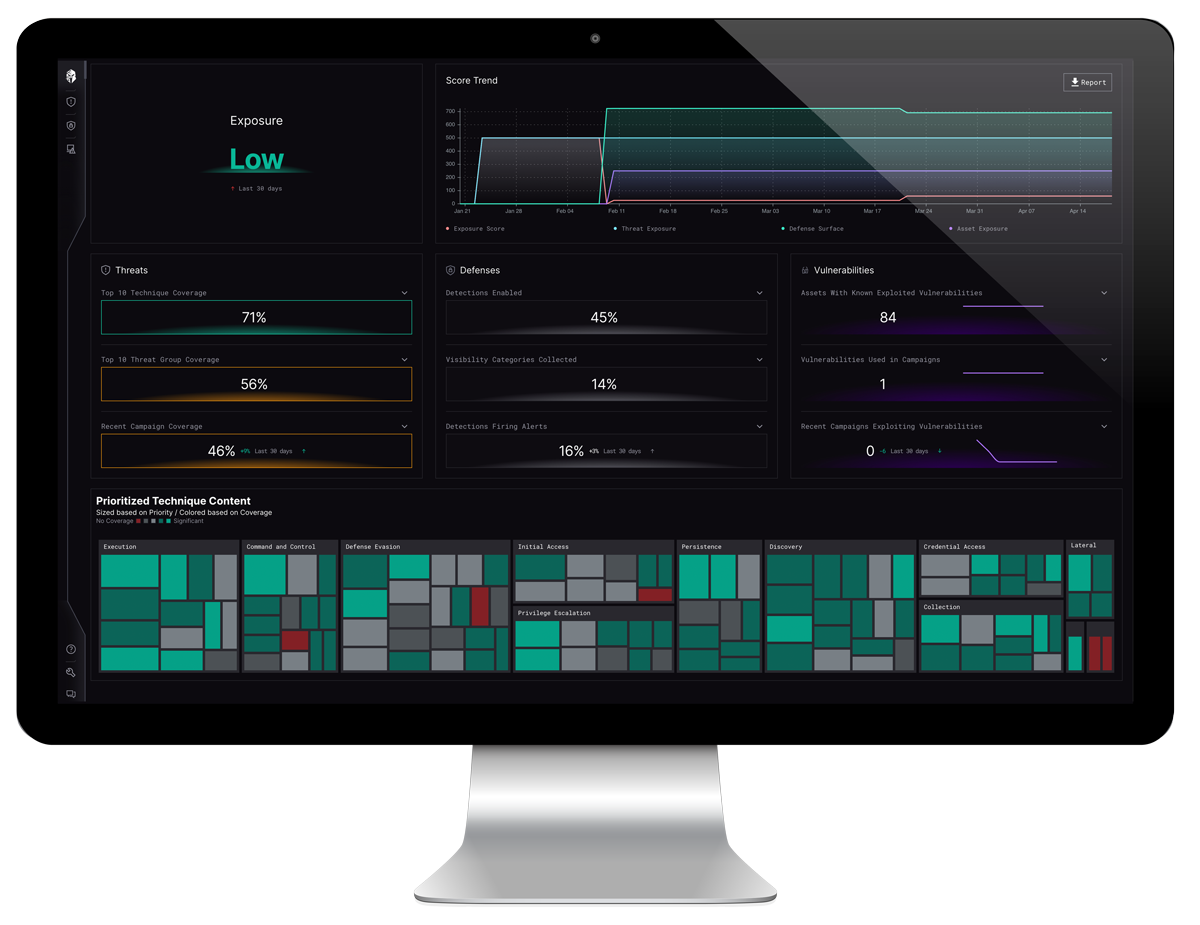
Microsoft reported that basic security hygiene still protects against 98% of attacks1.
However, organizations struggle with an effective patching program.
Why is this so hard?
The reality is that creating software is complex. With the creation of DevOps and CI/CD pipelines, organizations use and create software from multiple sources. A vulnerability can accidentally or purposely slip into an organization’s supply. Further, compounding the issue is the number of software programs that run in a modern enterprise. From desktop applications for business functions to specialized applications for infrastructure, the area that vulnerabilities can exist is massive. The patching program needs to cover a large environment and scale with the number of employees and systems.
Not all vulnerabilities are created equal
Malicious users have three basic objectives when they attack an organization: They want to “Get In”, “Stay in” and “Act”. This means that vulnerabilities that allow users to achieve those objectives have a higher target rate by adversaries.
For example, a vulnerability that allows the creation of a foothold (Get in), create an account (Stay In), execute commands (Act) will always be targeted more frequently than a vulnerability that doesn’t.

Of the thousands of vulnerabilities that organizations reported by their vulnerability scanners and process, the reality is that only 2-7% are targeted by threat actors. While most organizations are familiar with the Common Vulnerability Scoring Standard (CVSS), others may not be familiar with the Known Exploitable Vulnerability (KEV) list that is roughly 30% of known vulnerabilities listed in the CVSS. Fewer organizations are probably familiar with the Forum of Incident and Response Teams, FIRST (first.org) that has identified that only a low percentage of exploited vulnerabilities are actually targeted and exploited by threat actors as stated above.
Vulnerability intelligence is key to prioritization
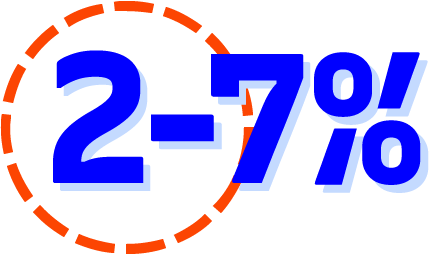
The key to prioritizing the 2-7% exploitable vulnerabilities is operationalizing and fusing threat intelligence with your security program.
A historical analysis of exploitable vulnerabilities, based on adversarial techniques, tactics, and procedures (TTPS), illustrates that adversaries overwhelmingly target vulnerabilities that allow them to gain command-line access/command shell. An adversaries’ operational profile, a combination of TTPs, targeted vulnerabilities, and preferred targets, then dictates the next portion of the 2-7%. The synthesis of this data is Vulnerability Intelligence.
Using a Continuous Threat Exposure Management (CTEM) program fused with vulnerability intelligence allows an organization to validate their cybersecurity strategy. CTEM is a program designed to measure and reduce risk exposure by discovering assets, prioritizing the most likely threats, and validating that a vulnerability is exploitable and the ability to mitigate is sufficient. Successful threat exposure management is built upon operationalizing TTP-based threat intelligence integrated with vulnerability data from sources referenced above, with analysis of the relationships between defenses, asset, threats, and vulnerabilities. Real-time situation awareness is gained through continuous exposure management and provides Vulnerability Intelligence on the threats and vulnerabilities most likely being used to target an organization.
CTEM combined with vulnerability intelligence is the ounce of prevention needed to prevent the pound of cure.
In Conclusion
Focusing the patch management activities against the threats that matter most allows organizations to operate left of boom in a proactive manner.
Learn how Interpres Security can help you automate and align your vulnerability management program with threat-informed vulnerability intelligence, so you can:
Know what exploitable vulnerabilities are being used to target you
Know what assets have vulnerabilities associated with active adversarial campaigns

Know what vulnerabilities should be prioritized and patched first
Know if your defense surface is prepared to mitigate exploitable vulnerabilities