This is Part 2 of our "Cybersecurity Is" Series.
Miss Part 1? Catch up here: Cybersecurity Is: Failing… How do we start to Win? – Part 1. Also, consider finishing the series with: Cybersecurity is Competition – Here’s the Playbook – Part 3.

Over the course of several decades of working with the military and the federal government, I hadn’t really thought of how much cybersecurity costs. Of course, I had been in discussions with the budget folks who wanted to know when we were going to stop buying things and actually make things better. We would brush the concerns off with pithy sayings of “The adversary only needs to be right once; we have to be right 100% of the time” or “The adversary gets a vote” or we would just ignore the comment and start talking about risk in this nebulous way and say “you just don’t understand.” Then we would request a budget increase, or additional monies, or we would deprecate some other program to pay for it.
The budget wars, or more appropriately – My security idea is better than your security idea (aka rob Peter to pay Paul) – was and is the general strategy for most things in cyber. It’s a cacophony of well-meaning professionals that have strong beliefs in their solutions or ideas. I’ll give you an example, if you had $1, would you spend it on spear phishing training (don’t click the link) or a spear phishing point solution? The same question could be asked about compliance frameworks, as an old boss of mine recently mused about the value of compliance frameworks and how many keep popping up.
Unfortunately, we are going down this path again, as most of us endorse the Security Exchange Commissions thoughts on mandatory cybersecurity expertise on the Board of Directors. We think this will help the Board understand the cyber risks and fund more projects. I’m afraid that’s not going to be the outcome. I think the unintentional consequence will be more turnover for CISOs or more misspent dollars. My reasoning is the same as above, if two people can’t agree on training vs point solution, what makes us think they will agree on any solution? Or if they do agree on a path forward, how do we know that is the right path forward? But that’s okay, we’ll just rip and replace when things don’t work out. And when the CFO asks what happened “Well, you just don’t understand” the choir will start to sing.
So what’s the answer? Threat-based cybersecurity – starting with data to make well-informed and defendable decision-making. Let’s break it down into two major phases – Situational Awareness and Decision-making.

In situational awareness – we are going to take a book from Sun-Tzu and focus on knowing our enemy and knowing our self. Look at the “security” data on your system – what logs are you collecting, what configuration files, vulnerability data, fleet management data – basically any data that can be coined “detection” data.
Know yourself:
- Telemetry data
- Configurations
- Logs
- Fleet Management
- Vulnerability management
Know your Enemy:
- What are their TTPs?
- What are their goals?
- What are their objectives?
Knowing yourself and the enemy is not a one-time event. Security Controls decay over time, adversaries change tactics, vulnerabilities fall in and out of favor and fleet management is a never-ending variable. Continous assessment of the external, internal, and that relationship is key to a comprehensive up-to-date situational awareness.
To finish this part of the situational awareness,
you must take the data from know yourself and know your enemy and translate them into a data set that can be used. We do this through the MITRE ATT&CK and NIST CSF frameworks to normalize the data against each other.
MITRE ATT&CK
Framework provides the rosetta stone to translate the multitude of TTPs into supersets.
NIST CSF
Provides the key to unlock your detection eco system across the MITRE ATT&CK framework. How does each detection support the Protect, Detect, Respond, Identify and Recover functions in accordance with the techniques listed in MITRE ATT&CK?
Decision-Making process starts with conducting a gap analysis of the adversary TTPs and the results from the NIST CSF Protect, Detect, Respond (PDR) mapping of your telemetry.
Then it’s simple to make fact-based decisions on the gap analysis from the results. Ask yourself three basic questions.
What capabilities are redundant, and can I remove them?
What capabilities can be repurposed, turned on, or create value in new ways?

What capabilities are we missing?
Now we can make fact-based decisions, show our work in simple ways to create understanding, and drive ROI metrics for every investment decision.
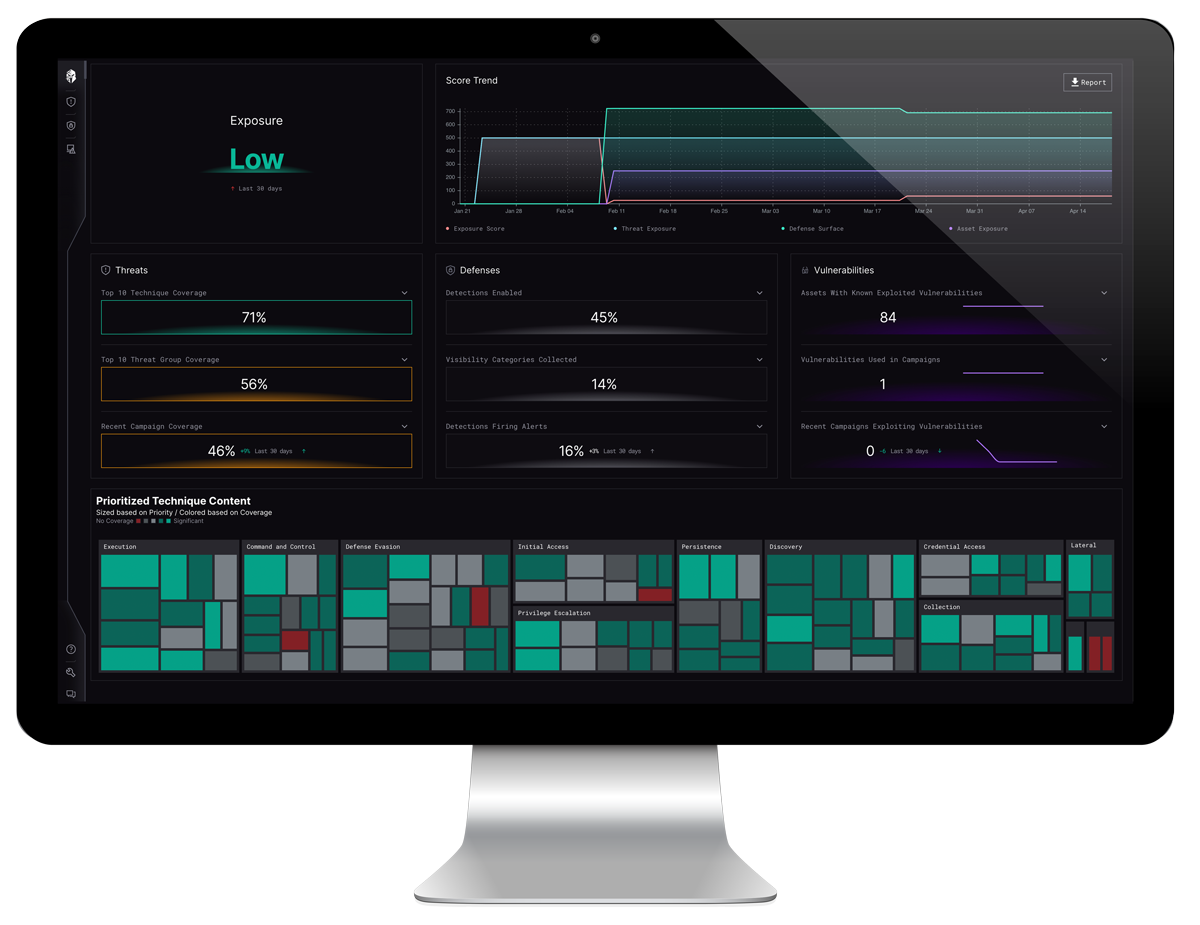
Why Interpres?
Interpres right-sizes your defensive strategy against the cyber threats that matter most. Our automated, evidence-based platform analyzes the dynamic relationship between your defensive capabilities and adversarial threats, prioritizes recommended actions and optimizes your security ecosystem. We provide an unbiased view of your security posture and continuously measure threat exposure so you can focus resources on the most relevant threats.