Summary
Recently U.S. Agencies released a Joint Cybersecurity Advisory (CSA), Multi Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475. Analysts confirmed that nation-state advanced persistent threat (APT) actors exploited CVE-2022-47966 to gain unauthorized access to a public-facing application (Zoho ManageEngine ServiceDesk Plus), establish persistence, and move laterally through the network. This vulnerability allows for remote code execution on the ManageEngine application. Additional APT actors were also observed exploiting CVE-2022-42475 to establish presence on the organization’s firewall device.
CISA, Federal Bureau of Investigation (FBI), and U.S. Cyber Command’s Cyber National Mission Force (CNMF) joint Cybersecurity Advisory (CSA) refers to Tables 3-13 for the APT actors’ activity mapped to MITRE ATT&CK tactics and techniques with corresponding mitigation and/or detection recommendations. CISA and co-sealers identified an array of threat actor activity, to include overlapping TTPs across multiple APT actors. APT actors attempted to exploit a known Apache Log4j vulnerability (CVE-2021-44228) in the ServiceDesk system but were unsuccessful.
Key Takeaways
- Malicious actors commonly scan internet-facing devices for vulnerabilities.
- Firewall, VPNs, and edge network infrastructure are attractive targets for attackers.
- Prompt patching of known vulnerabilities and robust access controls are critical for defense.
- Network sensor coverage and centralized data location awareness are important for effective incident response.
- Disabled administrative account credentials were used to evade detection, and NAT IP logging was not enabled.
Interpres Resources
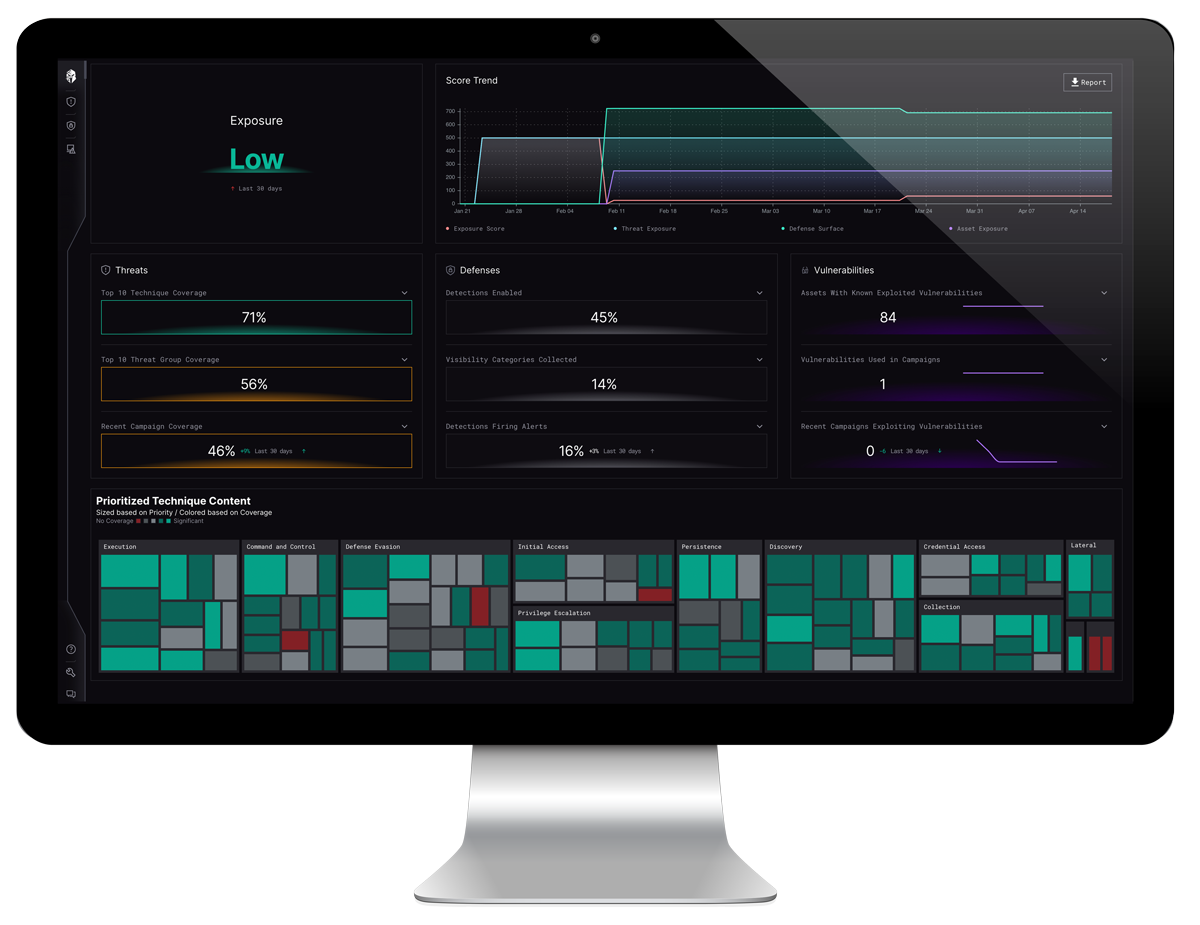
Interpres Security automatically ingests all CSAs and performs an automated “readiness” assessment tailored to an organization’s defensive capabilities. Interpres extracts all adversarial Tactics, Techniques, and Procedures (TTPs) detailed in the CSA and measures the risk exposure the organization has with regard to the identified campaign. See Figure. 1. below regarding this campaign.
Once TTPs have been extracted, Interpres analyzes your defensive toolsets, controls, and security logs to determine an organization’s readiness to defend against the identified TTPs. Interpres also measures fleet exposure by identifying assets present within the defended environment and prioritizing CVE patching efforts. Interpres allows for instant and continuous understanding of your organization’s risk exposure to adversarial campaigns while providing a prioritized mitigation path that is specific to your organization’s specific defensive capabilities.
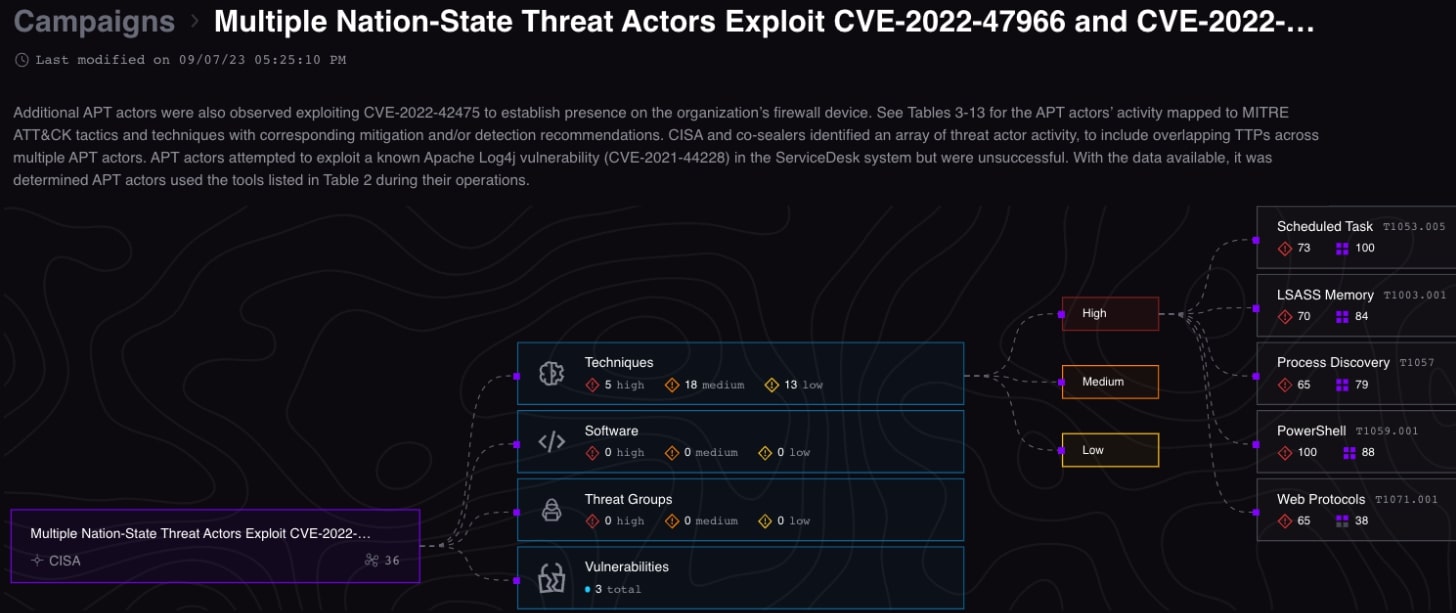
Figure 1. Interpres Threat Exposure Management Platform: Multi Nation-State Threat Actor Exploit CVE-2022-47966 and CVE-2022-42475
Automated campaign content was ingested by the Interpres platform and automated analysis revealed 39 total relationships, 36 techniques, and 3 vulnerabilities. Campaign content is mapped to an organization’s defense surface and assets to determine readiness and to evaluate and optimize security posture for threat mitigation, visibility, and detection.
See the ALERT: CISA, FBI, and CNMF Release Advisory on Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475, for additional information on this Advisory.