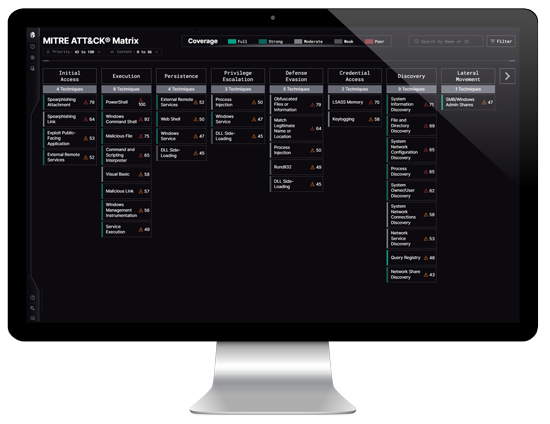
-
DPRK Exploits 2 MITRE Sub-Techniques: Phantom DLL Hijacking, TCC Abuse
Read MoreNorth Korean hackers break ground with new exploitation techniques for Windows and macOS…

-
MacTech News: As macOS Malware Grows In Popularity, Windows Exploits Remain Another Vector of Choice For Threat Actors
Read MoreAs the macOS desktop user base continues to grow year over year, and Windows remains a mainstay, adversaries are growing more adept in their strategies to become more versatile cross-platform…

-
Apple World Today: As macOS Malware Grows In Popularity, Windows Exploits Remain Another Vector of Choice For Threat Actors
Read MoreAs the macOS desktop user base continues to grow year over year, and Windows remains a mainstay, adversaries are growing more adept in their strategies to become more versatile cross-platform…

-
Return of the mac(OS): Transparency, Consent, and Control (TCC) Database Manipulation
Read MoreAs the macOS desktop user base continues to grow year by year, adversaries are adapting their strategies to become more cross-platform. Gone are the days when macOS was considered immune to malware. This report delves into the evolving landscape of cyber threats, focusing on adversarial techniques aimed at manipulating the Transparency, Consent, and Control (TCC) framework database.

-
Windows Phantom DLL Hijacking: Turning “Nonexistent” DLLs into Real Threats
Read MoreThe Windows operating system (OS) references a surprising number of DLL files that do not exist. Thus, phantom DLL hijacking occurs when the adversary names their malicious DLL to match the non-existent file and writes it to the specified location of one these referenced missing files.

-
Interpres Security Threat Intelligence Engineer Marina Liang publishes research on APAC Hackers Hijacking Windows DLL & Abusing macOS Security Framework
Introduction As the macOS desktop user base continues to grow year over year, and Windows remains a mainstay, adversaries are growing more adept in their strategies to become more versatile...Read Blog
-
Interpres Security Successfully Completes SOC 2 Type II Certification
Read NewsThird-party audit validates Interpres’ commitment to security and compliance.

-
Let’s Celebrate World Backup Day 2024
Read MoreHear From Industry Experts – This year’s World Backup Day, which falls on March 31st, 2024, is a prime opportunity to re-evaluate your backup strategy…

-
Interpres: The Missing Intelligence Layer for CTEM
The Gartner Continuous Threat Exposure Management (CTEM) strategy is designed to capture the outputs from specific products in the security stack to improve security processes and continuously reduce risk while...Read Blog
Interpres Security operationalizes TTP-based threat intelligence and automates continuous exposure monitoring to help CISOs and security practitioners reduce threat exposure. The Interpres Threat Exposure Management Platform analyzes the dynamic relationship between defensive and adversarial capabilities, assets, and their exploitable vulnerabilities; prioritizes the required defensive actions; and optimizes the security environment, to provide continuous threat exposure management.