FBI Director Christopher Wray in his opening statements (Director Wray’s Opening Statement to the House Select Committee on the Strategic Competition Between the United States and the Chinese Communist Party — FBI) testified to the PRC’s pre-positioning of stealth implants in our critical infrastructure with the intent to use them to disrupt not only U.S. Foreign power, but also to undermine the very fabric of the day-to-day life of American citizens.
The PRC has been and continues to use cyber tradecraft to advance their economic and regional position in the global economy. Chinese APT groups target every facet of the U.S. and its allies socio-political and economic pillars. From collecting of data from TikTok to fuel their Artificial Intelligence development to theft of intellectual property to advance their strategy of China 20251.
Director Wray testified that the PRC hacking units outnumber the totality of the FBI cyber forces by 50-1. An organization this highly resourced, professionalized and determined is unlike anything most of the U.S. private industry, let alone critical infrastructure, has ever faced. The ability to investigate, discover, and weaponize zero days and other tradecraft cannot be underestimated or ignored.
Why Critical Infrastructure?
The PRC is targeting U.S. critical infrastructure to cause harm to the American people and by extension their will to support U.S. policy in the Indo-Pacific region. PRC Military Doctrine on asymmetrical warfare clearly discusses the need to delay any U.S. deployments to the region, and questions whether the American people would support a conflict if California was without power and water.1
PRC, Volt Typhoon and Living off the Land
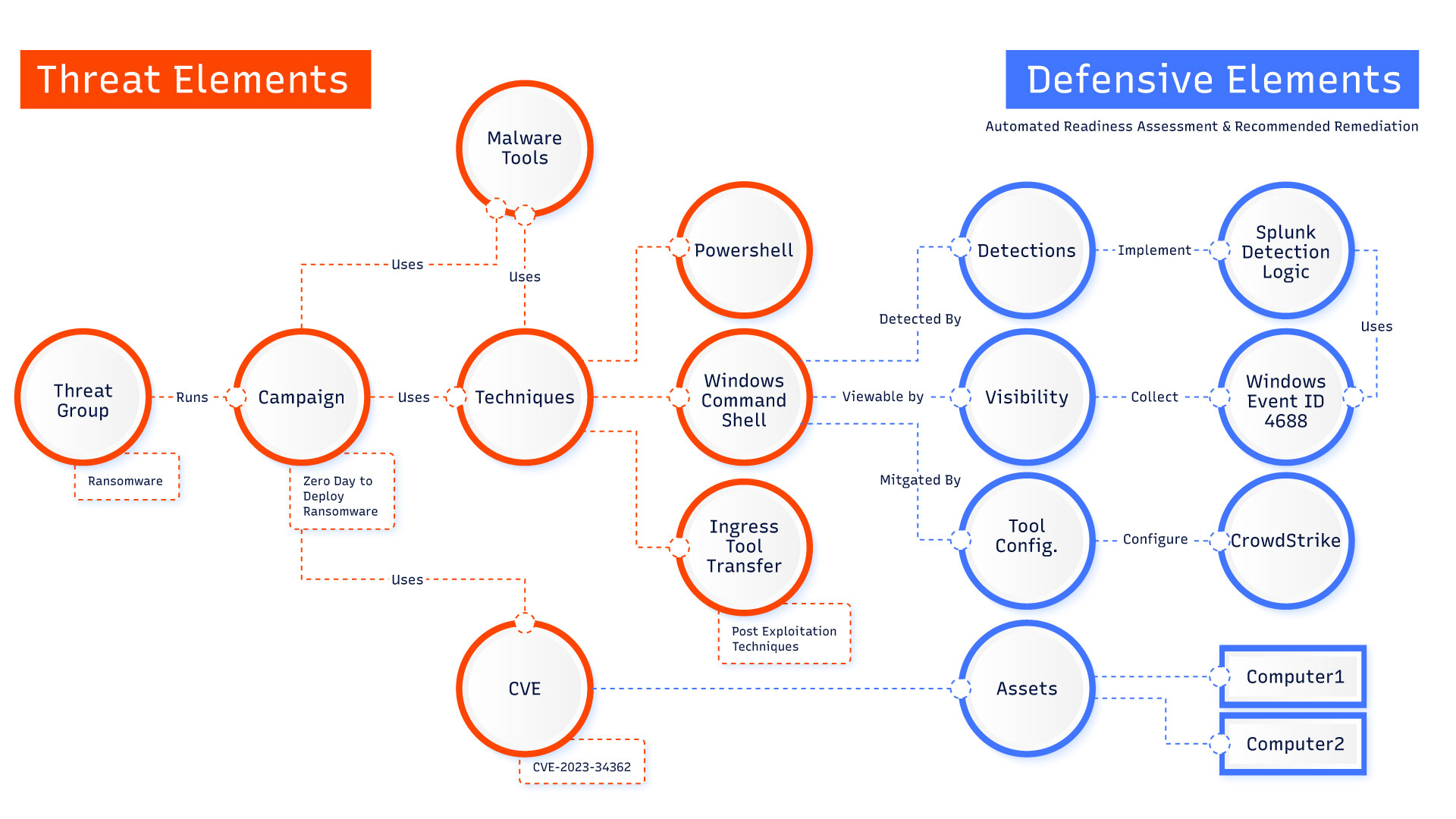
The PRC’s latest campaign, Volt Typhoon, utilizes the nature of the internet as a hyperconnected system-of-systems to infiltrate critical infrastructure across the U.S. hacking small business and home office (SOHO) routers deployed to people’s home residence by internet providers allowed the PRC to effectively “ride” legitimate connections upstream into their targets. Once they achieved a foothold on the deployed routers, they used legitimate commands to evade detection by security products – aka “Living off the Land.”
Trust but Verify

The first step is verifying that your security strategy is designed to stop threat actors that are targeting you. Use Techniques, Tactics, and Procedures (TTPs)-based threat Intelligence to understand who, how and where adversaries are most likely to target you. Ensure the development of a robust threat model to align the adversaries TTPs to your environment. Conduct a defensive readiness assessment, mapping your controls to the adversaries’ TTPs, identify any gaps, overages, and areas of improvement.

Second, plan for the dynamic relationship of threats, vulnerabilities and defensive controls. The corporate network is in a state of entropy; threat actor TTPs change, new vulnerabilities emerge, security controls and products are accidentally turned off, updated, or modified without the knowledge of the SOC or CISO. Maintaining a live situational feed of any change in that state is key to limiting exposure to threat actors.

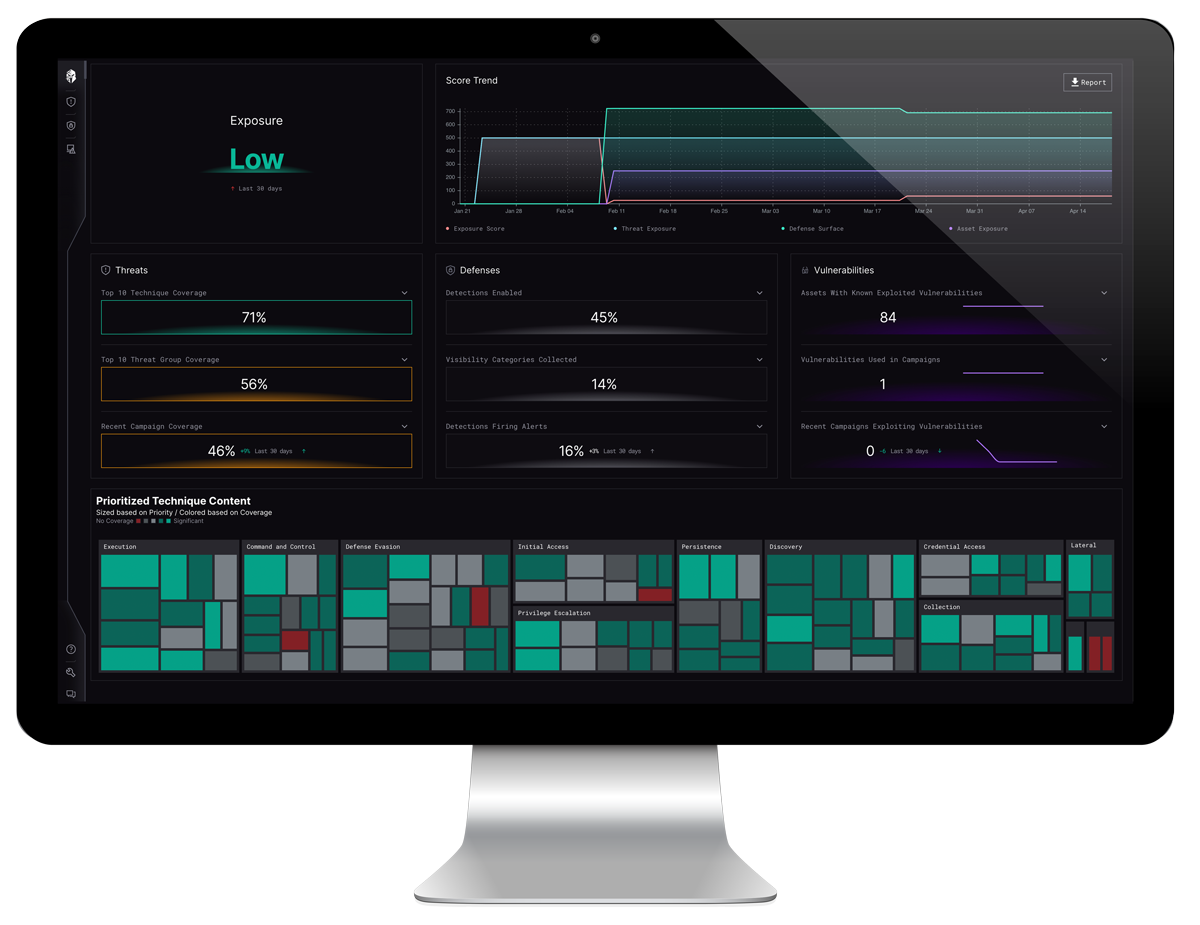
Third, having a robust visibility and detection program that identifies gaps, changes and opportunities to improve ensures that your organization is ready for any vector of attack.

Fourth, use vulnerability intelligence to prioritize your patch management activities. Vulnerability Intelligence is understanding which vulnerabilities and adversary is most likely to exploit, the tradecraft to do so, and the impact of the vulnerability. Adversaries overwhelmingly target vulnerabilities that allow them to gain command-line access/command shell. Limit those processes to key personnel and wrap the processes with detection logic to ensure if an unauthorized entity executes, the SOC will be notified.
Conclusion - Are you ready?
With the current direction of the PRC Communist party, this situation will continue. Defending yourself is more than a cybersecurity or business decision… It is one of national security. Ensuring your defensive readiness is at its optimal state is key to limiting the PRC’s damage to U.S. economic and national security, as well as ensuring that your business continues to compete in the national and global markets. How is your organization currently assessing and validating your cyber defense readiness against prioritized threats like this?
Assess & Validate Your Defensive Capabilities
Learn how the Interpres Defense Readiness solution can help you understand your defensive capabilities and automate the cyber readiness process.