Over the course of my time as the Department of Defense (DoD) Cybersecurity Analysis and Review (DODCAR) Chair, I gave a lot of briefings on the process that DoDCAR follows. My Predecessor, Chair of the NIPR/SIPR Cybersecurity Architecture and Review (NSCSAR), did the same, but also made YouTube videos of the process (Strengthening Practices: NIPRNet/SIPRNET Cyber Security Architecture Review – YouTube) – The point of this blog is not to go into as much detail as Pete’s video, but rather highlight the major steps that go into a Defense Readiness Assessment (DRA), and conduct an assessment that yields accurate results and actionable data.
First, we have to understand what a DRA is. At its basic form a DRA is an outcome of determining whether your security controls and capabilities are sufficient to protect, defend and respond (P/D/R) to a given threat. DRA is also known as “Proof Positive, Proof Negative” exercises or a Request for Information (RFI) that should measure your exposure to a given threat or families of threat.
Benefits:
- Conducting a manual DRA provides the organization with a basic understanding of their ability to protect, detect and respond to a given threat or threat event
- A snapshot in time to communicate risk to the board of directors and executive stakeholders
- Excellent way to conduct stack consolidation
Negatives:
- A manual assessment takes 4-6 weeks to conduct
- Risk of being overcome by events due to time length
- Can be subjective and influenced by vendors
What Triggers a Defensive Readiness Assessment (DRA)
DRA’s are traditionally triggered by a threat report but can be triggered by a threat event or RFI. A threat event scenario is when the board of directors or CISO wants to understand the organization’s security posture and whether the business assets are protected against a threat scenario that appeared either in headline news or in a competitors’ network. As general parlance, CISO’s refer to this as a Proof Positive, Proof Negative exercise, and generally are composed of the starting question “Could this happen to us?”.
DRA’s triggered by a threat report are more straightforward. Cybersecurity and Infrastructure Security Agency (CISA) or a reputable, national level organization releases a threat report or advisory either around a major Vulnerability (e.g., Log4J) or around a threat-level campaign (e.g., MoveIT). Organizations then conduct a DRA to determine their risk exposure to the threat, associated vectors, and their ability to defend against it.
DRA Steps
A DRA is defined by 5 major steps:

Creating a Threat Model
The first step in conducting a DRA begins with understanding whether a threat event or report is applicable to your organization. Which means we have to build a threat model of our organization.
The threat model can be relatively basic but is important, as hacking groups have become specific (and opportunistic) in their targeting. Key attributes for your threat model should include:
- Size of organization
- Geographic operations area
- Operations sector (manufacturing, healthcare, financial, etc.)
- Type of data being protected (HIPAA, CUI, PII, ETC)
- IT infrastructure major component groups (Cloud, Mac, Windows, remote connectivity, etc.)
- Applicable governance, risk and compliance (GRC) mandates
Once the threat model is complete, it becomes the first gate in your DRA. When CISA JCA (Joint Cybersecurity Advisory), “PRC Living off the Land” was published, the report was specific in that the PRC (VOLT TYPHOON) was targeting ICS/SCADA systems in the Pacific Rim via remote telework. If the threat model included Pacific Rim (Geography), IT Infrastructure (Remote work), and ICS/SCADA data – it was time to move to the next step. If not, the assessment was completed.

Assessing the Threat
The importance of creating the threat model allows us to focus on the threats that matter most, i.e., creating an empirical understanding of the threats that are targeting us, instead of attempting to understand all threats. This step includes collecting ALL relevant threat data that matches our threat model – best places to start are CISA JCAs, but breach reports from the major cybersecurity and telecom organizations work as well. We want to use threat reports that detail the “Who” and “How” the adversary is attacking and their tactics, techniques, and procedures (TTPSs). If you are familiar with the Pyramid of Pain, TTPs are the hardest pieces of intelligence to work with, but they are the hardest for adversaries to change. The lowest level, atomic indicators of compromise (IoCs) are easy to plug into a firewall but are extremely easy for the adversary to change. Changing how they do something requires reprogramming tools, culture and methodology. Much more difficult to change, however, the MITRE ATT&CK Framework gives us the capability to build a heuristic on the TTPS that we need to assess.
Once we have all the relevant intelligence, the team will go through the intelligence and make a heuristic (aka heat map) by checking the applicable MITRE ATT&CK layer 3 TTP box. Repeating this process through the entire intelligence collection, this will give us the prevalence of TTPs and associated prioritization when we get to step 5. If the DRA is only for specific Proof Positive, Proof Negative or RFI – the heuristic will be simple checks.

Identifying Targets
Identifying targets is sometimes viewed as an optional step. This step is understanding what CVEs an adversary has shown preference to target or what CVE’s have the most significant impact on the network. Organizations treat this step as optional predominately because of the inability to prioritize a given vulnerability.

They have over 10K vulnerabilities slated for patching, but without an understanding of what can really hurt them, the act of attempting prioritization is relatively futile.
However, understanding that only 30% of all known CVEs have a published exploit (CISA KEV), and of that 30% only 2-7% are actively targeted (www.FIRST.org), drastically reduces where an adversary can target.

Assessing Defensive Capabilities
Continuing with the DRA, Step 2 identified the “Who” and the “How”, while Step 3 identified the terrain that will be attacked. Step 4 is about quantifying defensive capabilities. To start this step, map your defensive capabilities against the MITRE ATT&CK framework. Once this is done, each mapping needs to be divided into P/D/R in the framework. The Protect function is a checking of the configuration of security appliances as security entropy will see controls becoming non-compliant for many reasons.
The Detect should be further sub-divided into Visibility and Detection Logic, as an organization may have the telemetry available, but not the Detection logic built and deployed. The Respond function may or may not be applicable depending on a company’s Zero Trust transformation. The P/D/R functions scoring can be simplistically colored Green (Good coverage), Yellow (Medium Coverage) and Red (Poor coverage) marked for remediation.

Measuring the Gaps
Taking the Threat Heat Map generated in Step 2 and comparing it to the Defensive Capability Map in Step 4, will present a basic understanding of the DRA. An organization will have a pretty comprehensive map of how the adversary will attack them, and how well they can P/D/R against that threat. The organization can then move into remediation phase.
Summary
Conducting a manual Defense Readiness Assessment is a lengthy and highly intensive effort that can pay off dividends in stack consolidation but can be sidelined by lack of prioritization, vendor influence, and intervening events. Organizations that conduct DRAs usually spend 4-6 weeks for each CISA Advisory or major breach report.
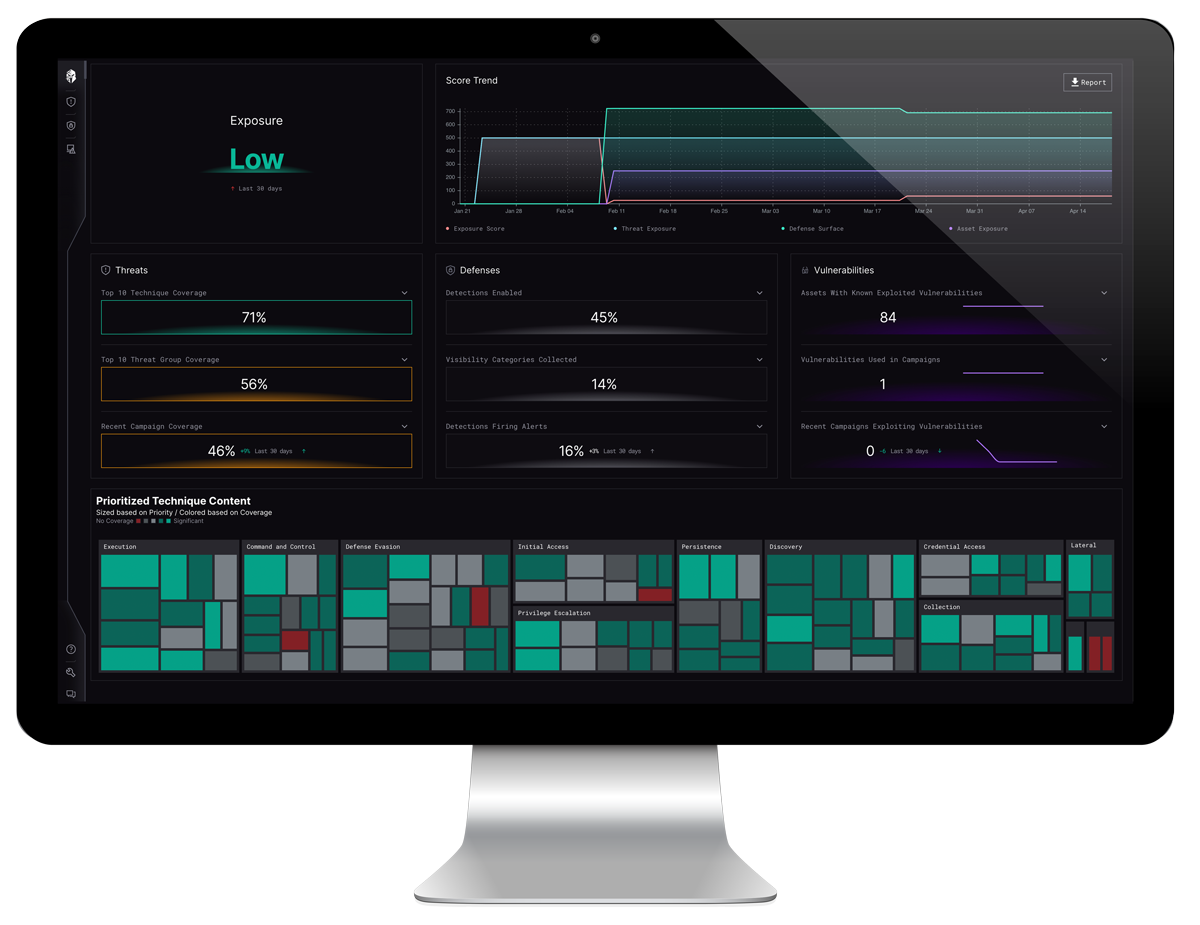
The automated Defense Readiness assessment capabilities of the Interpres Exposure Management Platform reduces time, resources and eliminates vendor influence by reaching a speed and scale to reduce a 4–6-week exercise into a 1-hour event, that provides continuous monitoring of state between threat, vulnerability and defensive Controls.
Learn how Interpres Defense Readiness solutions can help you understand your defensive capabilities and automate the cyber readiness process or take a product Test Drive and see for yourself.
About Interpres
Interpres optimizes your defensive strategy against the cyber threats that matter most. Our automated, evidence-based platform analyzes the dynamic relationship between your defensive capabilities and adversarial threats, prioritizes recommended actions and optimizes your security ecosystem. We provide an unbiased view of your security posture and continuously measure threat exposure so you can focus resources on the most relevant threats.