Cyber defense strategies typically follow a generalized, one-size-fits-all approach that has repeatedly resulted in failure. This is evidenced by the losing battle against adversaries who continue to refine their tradecraft, costing businesses billions of dollars between the usual outcomes of data breaches, ransomware attacks, and IP theft. Add to that the fact that security professionals are still manually collecting data in spreadsheets in order to correlate defense readiness data from SIEMs, EDRs, and a host of other security tools in their stacks. Clearly, it’s time for a new approach.
Defense Optimization – Data Does The Trick
Understanding your defense readiness first starts with coming to terms with your organization’s own limitations, which typically include budget and engineering capacity constraints. Because of this, it’s vitally important to focus on the threats that matter most. This involves implementing a threat-informed defense (TID) methodology. This methodology allows organizations to prioritize the threats that are most likely to impact your organization. At the same time, it takes into account the capabilities of the tools you already have in order to quantify your exposure, shift controls, and rationalize your security ecosystem.
For the uninitiated, this may sound simple enough, but behind the scenes there are constantly evolving relationships between the threat landscape and your defense surface. That’s why automating this process is so important. A proactive TID strategy integrates knowledge of known tactics, techniques and procedures (TTPs) to guide the development and prioritization of defense mechanisms. Your threat profile – details of who you are such as industry, geographical location, and the platforms you utilize – determines the threat landscape you face. Whether you’re a small manufacturer in the midwest, a multinational financial institution, or regional hospital; these characteristics will determine the threats you face and the TTPs most likely to be used against you.
Once you understand your threat profile and your defense surface, the real work begins – but that doesn’t mean it has to be hard work. With the power of automated tools, we can work smarter.
Grinding Gears – The Manual Way
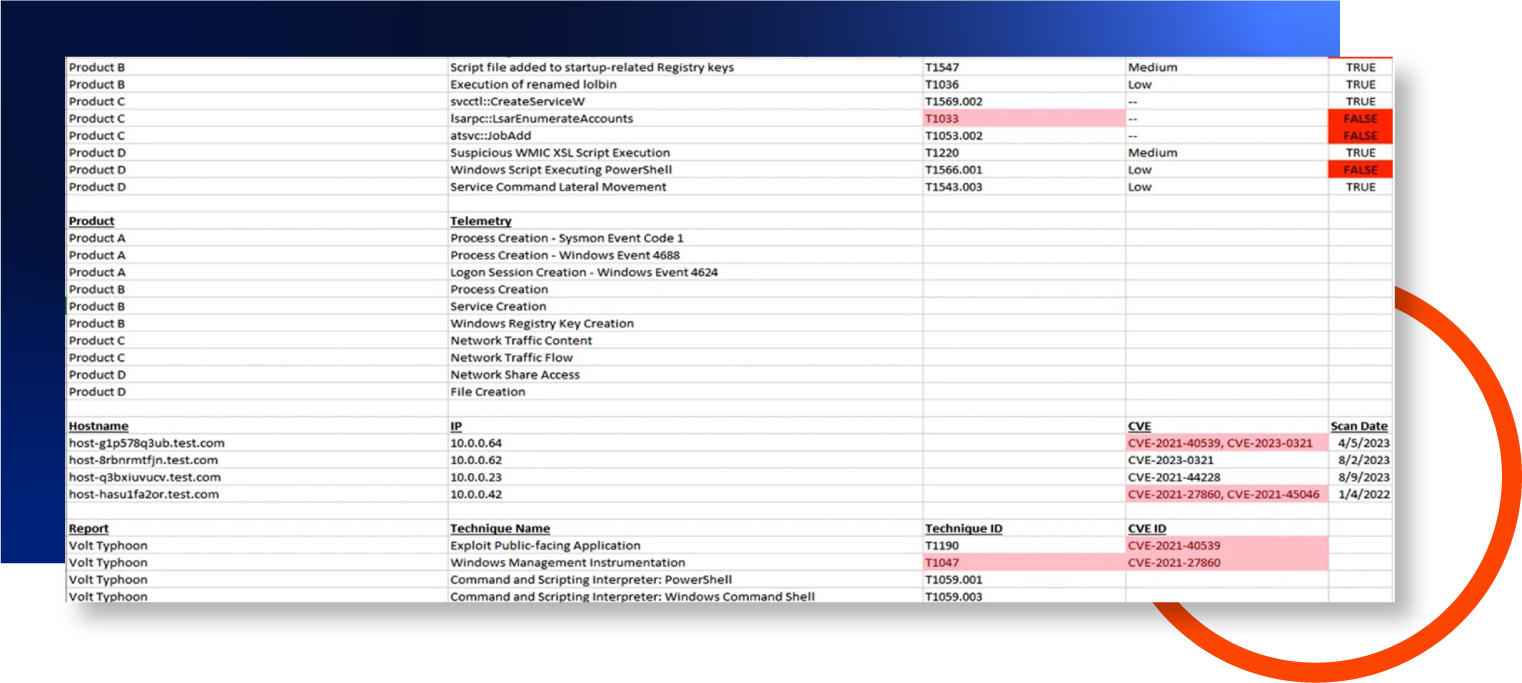
This process is something that can be done manually with Excel (and maybe a stiff drink). However, you’ll find that when you go home for the day, the Earth rotates and you get back to work the next day just to find that yet another new CISA advisory or a critical CVE has been published. At the executive level, leaders want to know if their company is vulnerable, if they’re ready to defend, and how they can harden their defenses. Meanwhile, on the security operations floor, practitioners are looking into the TTPs the adversary is using, what detections and controls are in place and what assets are vulnerable – two sides of the same coin.
So the work begins by parsing the threat report, logging into all of the security products to determine if the current preventative controls apply, logging into vulnerability management products to find exposure within the fleet, and throwing that information manually into a spreadsheet.
This can take anywhere from 72 hours to two weeks per report. Even then, the spreadsheet is just a snapshot in a point of time. Again: We go to sleep, the Earth rotates, and there’s a new report. It’s simply not scalable.
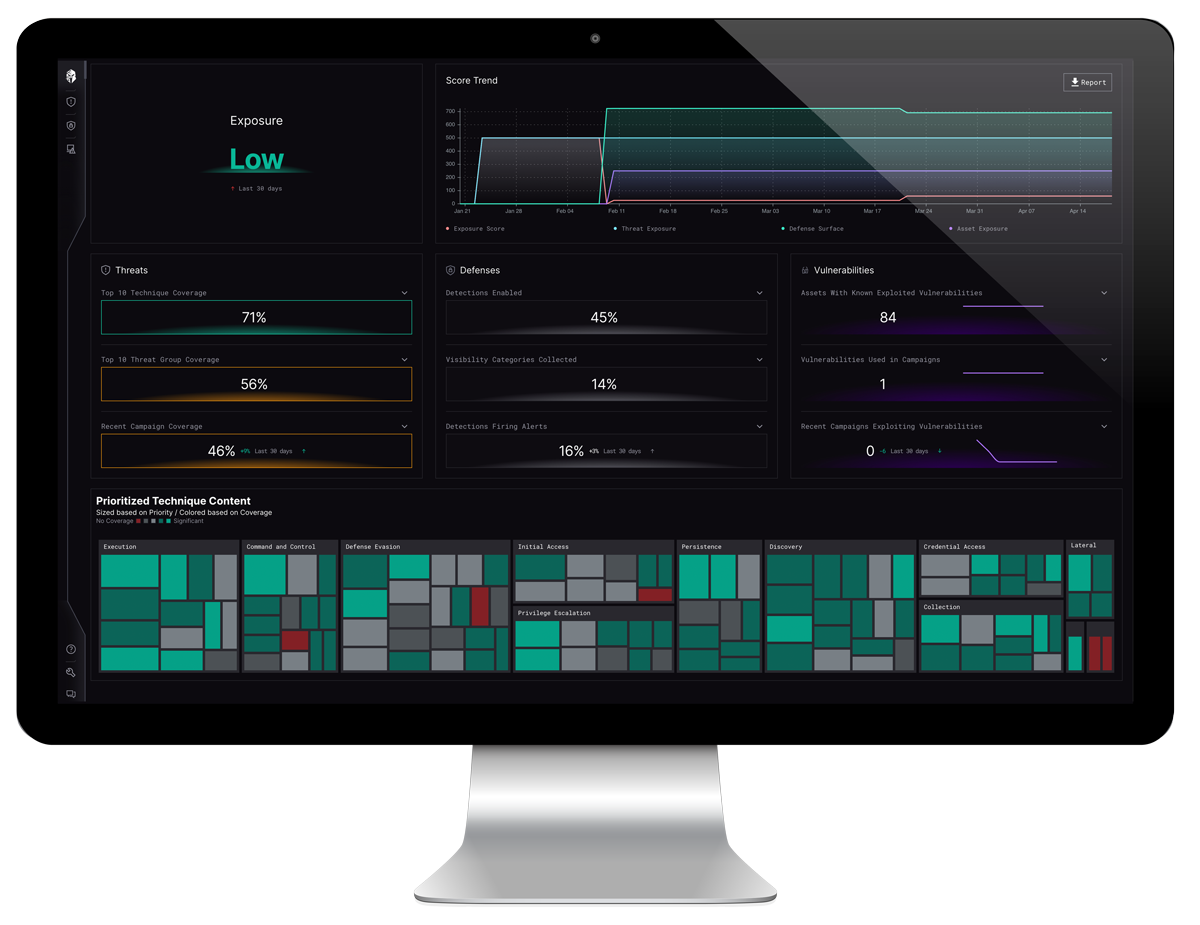
A Smooth Transition – The Interpres Way
At Interpres, we want to make the process of defense readiness as smooth as possible for security teams so that they know their posture at any given point against any given threat.
Interpres helps security teams with:

Defense Readiness:
Prioritize the threats targeting your organization
Defense Surface Optimization:
Automate the relationship between your controls and detections against adversarial TTPs
Vulnerability Intelligence Prioritization:
Highlight the exploitable vulnerabilities your adversaries are targeting across your fleet

Executive Reporting:
Communicate risk exposure as a sum of your operations, technology and exposure to leadership
Through automated processes that link your controls and fleet with the threats targeting your organization, we’re able to maintain continuous, holistic situational awareness of the dynamic threat landscape. The days of the manual spreadsheets are over!
Watch to Learn More
To learn more about how Interpres can reduce your time manually analyzing security technologies and protective policies from hours to minutes a day, check out the On-demand Webinar – Optimizing Your Defense Surface: From Manual to Automated hosted by Interpres Co-founder & Head of Research, Ian Roth.