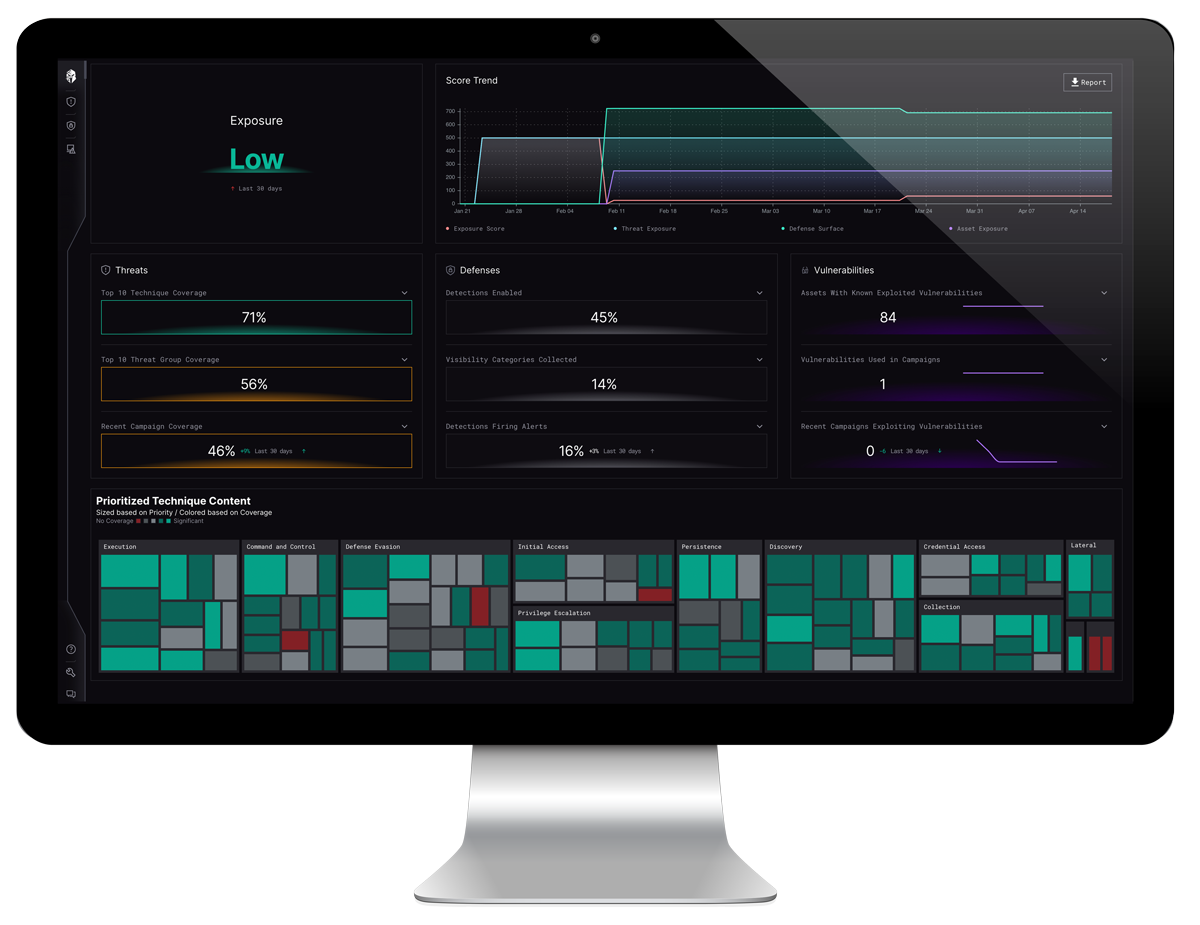
20+ years ago, when breaches and cyber events were categorized by worms and viruses, the phrase “Cyber is borderless” was invented. Because we did not know where the worms and viruses were coming from, we assumed that they could come from everywhere.
The bias of Cyber is borderless, extends into our subconscious and subsequently into our cyber defense planning processes of today. We focused on where attacks were coming from, namely IP addresses and domains. We didn’t have the information on hacking groups, their techniques, tactics and procedures, their preferred vulnerabilities to target or their operational ethics. However, as threats changed from worms and viruses to APTs and ransomware gangs, borders began to emerge. Some were geographical, but most were logical. APTs and ransomware gangs focus on specific business sectors and targets. They’ve developed well defined (and hard to change) techniques, tactics, and procedures, and they have developed affinities for specific vulnerabilities. We need to consciously remove the bias that cyber is borderless and embrace these new realities. We need to change the paradigm of how we think about these threats.
When we start to embrace the fact that adversaries use defined techniques, tactics and procedures, we are no longer held to the assumption that we need to buy yet another point solution that is the next magic bullet. Instead, use what you already have, in an optimized way. We can move away from planning bound by “The adversary COULD do X” to a planning function focused on “What adversaries are targeting me, and they are most likely going to do Y”. When we underpin our planning assumptions with “most likely”, it becomes easier to evaluate our investments in capabilities against what is “likely”, resulting in pinpointed investments and the ability to combat cybersecurity sprawl. This allows us to focus our budget and resources against the threats that matter most, versus all threats. We can focus on optimization against a known threat versus attempting to spread our resources thin by trying to address all threats.
Organizations are inundated with vulnerabilities to remediate and patch, and depending on the sector, some even have regulatory measures that mandate the patching of all vulnerabilities. Organizations may have upwards of 10,000 vulnerabilities currently in their queue, however, if we take the recent MOVEit incident as an example of the adversaries’ preferences, we can see that only 2 of the 6 CVE’s identified were actually targeted. An organization attempting to remediate all 6 listed CVE’s was wasting time from actually defending against the 2 CVEs and subsequent efforts that really mattered to defend against MOVEit.
This should not come as a surprise, as data collected by CISA under the Known Exploited Vulnerability (KEV) list shows that only 30% of all vulnerabilities have an exploit. Furthermore, FIRST.org has shown that only 2-7% of vulnerabilities are actually targeted.
The concept that “Cybersecurity is borderless” also focuses us to right of boom activities. CISOs know they do not have enough resources to combat all potential threats, so they focus on reducing dwell time, remediation, and returning to normal business functions, the foundation of zero trust. The industry has followed suit by creating more point solutions and focusing automation at boom and to the right of boom. The understanding that we can’t get ahead of the problem so we have to automate to limit the damage is flawed. We are subconsciously planning right of boom. We are reactively planning based on the latest news, threat or incident report. However, when we start to plan by using the known facts that adversaries operate within borders, defined TTPs, and preferred vulnerabilities we shift our
planning from right of boom to left of boom. In effect, we can start to be proactive against the threats, since we know what matters most. We can shift adversaries, exposure and readiness to the left of boom. Our planning functions focus on proactive defense versus reactive remediation. Now we can start to look at automating the functions of proactive defense, namely defensive readiness.
What’s needed is an automated and continuous Defensive Readiness capability that assesses our defensive capabilities against the threats that are constantly morphing and most likely to target us. Defensive Readiness is our ability to quickly and accurately gauge our ability to protect, defend and respond to an emerging threat. With MOVEit, the ransomware gang established a deadline to respond of 2 weeks. Most companies using manual efforts (i.e. spreadsheets) to track their controls and configurations against the threat took 2-4 weeks resulting in over 300 companies and 60M people (and still counting) being affected by MOVEit.
Companies that worked with Intepres to automate defensive readiness and shift the adversary left of boom spent 1 hour to measure their defenses and move into remediation.
They were prepared and successfully protected their organization from the threat that mattered most. CISOs constantly respond to board queries of “Are we vulnerable to that?” In effect asking, is our tooling optimally configured to defend us?
Changing to a paradigm of Cybersecurity with borders and well-defined threats, that operate with established TTPS and targeted vulnerabilities allows us to answer the question of “are we ready” in minutes, optimize our defensive capabilities, and utilize vulnerability intelligence to shift our planning focus to left of boom.
About Interpres
Interpres optimizes your defenses against the cyber threats that matter most. Our automated, evidence-based platform analyzes the dynamic relationship between your defensive capabilities & adversarial threats, assets & vulnerabilities. We then prioritize recommended actions to harden your defenses against prioritized threats and optimize your hybrid security ecosystem.
We provide an unbiased view of your security posture and continuously measure threat exposure so you can focus resources on the most relevant threats targeting you. Interpres works with your existing stack, it’s agentless, sensor-less & takes one hour to set up and run.

Watch to Learn More
To learn more about how Interpres can help you make the proactive shift to left of boom, check out the on-demand webinar: Are You Prepared? Aligning Your Cyber Defense Readiness to Threat Exposure featuring Interpres Chief Strategy Officer and Chief Evangelist, Pat Arvidson.