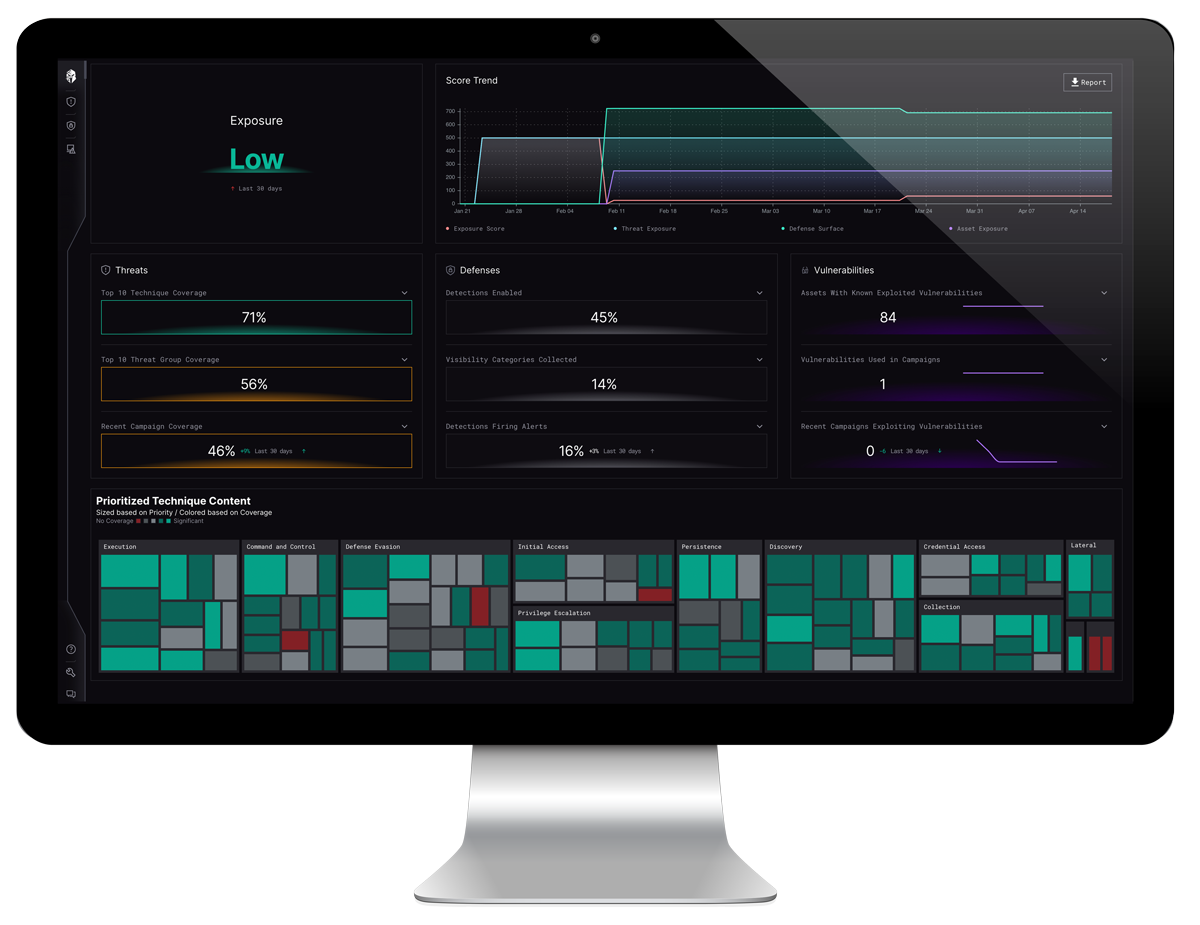
Quickly identify gaps in your defense posture

Accurately Measure and Tailor Your Security Defenses
Ensure Defensive Capabilities Are Aligned to Key Threats
- Map adversary behaviors to your defenses.
- Assess visibility, detection capability, and security tooling against relevant threats.
- Quickly identify gaps, misconfigurations, and hidden capabilities.
- Continuously monitor threat entropy across your environment.


Track and Remediate Changes in Your Environment
- Maintain situational awareness to detect changes in your tech ecosystem.
- Know what changed across your security stack—configurations, detections, controls, and log collection in real-time.
- Understand how changes in your environment affect your security posture.
Save Critical Time and Resources with an Optimized Security Strategy
- Optimize your ecosystem to prevent, protect, detect threats in the right places saving critical time and resources.
- Know what vulnerabilities to patch, security controls to enable, and security tool configurations to mitigate threat.
- Leverage reference detection logic to expedite your detection engineering process.

Know the Strengths and Weaknesses of Your Security Program
Surface missing telemetry
Identify changes in your environment and get insight on the impact to your security posture.
Get recommended actions to bolster defenses against the threats that matter most.