In 2015, officials from the DoD and NSA asked one simple question that served as the catalyst for Threat-Informed Defense (TID) and Continuous Threat Exposure Management (CTEM): “Are we managing the constantly changing relationship between threat and defensive controls to continuously drive down risk?”
Now, in 2023, many organizations are realizing the value of a threat-informed approach and are looking at ways to implement TID and CTEM programs in tandem. But it’s not without challenges and often times teams struggle to produce the results needed of a dynamic threat environment.
Challenges of Implementing TID and CTEM
Operationalizing a TID strategy requires significant investments in time, budget, personnel and technology. Meanwhile, the cyber talent gap is wider than ever, as the industry remains short-staffed and talent is in high demand. A rapidly changing threat landscape makes time a high-value commodity. The only way security practitioners can effectively handle the dynamic relationship between the threat landscape and defensive strategies is through the smart use of automation.

We’ve heard the feedback from CISOs and industry insiders, which is why we created the missing link to their CTEM program: Defense Surface Management (DSM).
What is DSM?
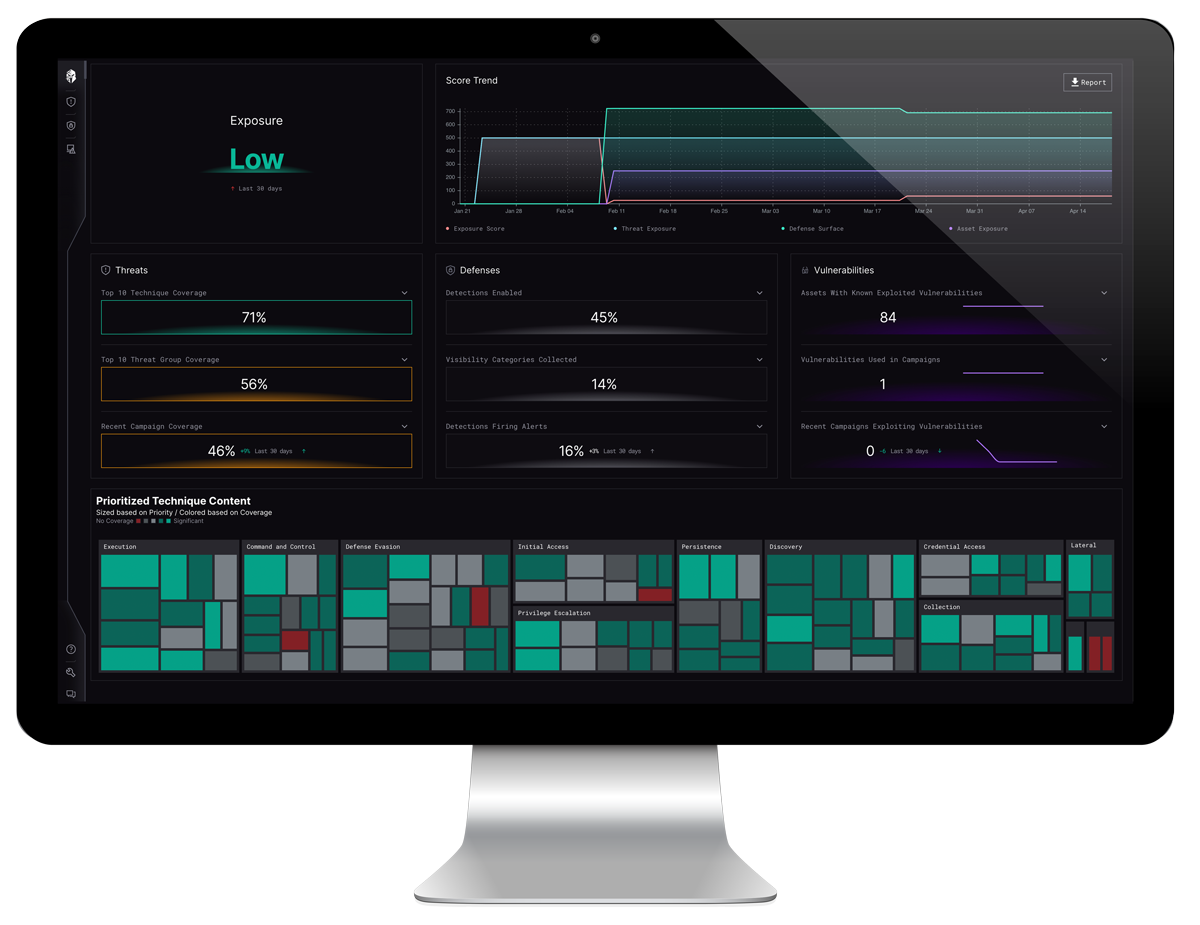
Defense Surface Management automates the laborious and time-consuming process of operationalizing TID while combining and contextualizing information sourced from CTEM tooling, defensive capabilities, and threat data. It functions as an intelligence layer that empowers organizations to continuously scrutinize the dynamic interplay between threats and defenses. The comprehensive analysis provided by DSM enables organizations to analyze, prioritize and optimize their defenses, thereby reducing threat exposure in a manner that is both efficient and effective.
DSM begins by analyzing your specific organization’s threat profile based on a number of factors including company size, industry, protected data and more. From there, DSM baselines your specific defensive capabilities and calls out the strengths and weaknesses. Next, DSM compares your capabilities against the adversarial TTPs that are most likely to affect your organization, creating a battle map to show critical vulnerabilities for you to act on and reduce threat exposure. Finally, DSM scraps the “one-size-fits-all” approach to continuously optimize your controls to defend against the threats that matter most.
This cycle continues automatically to make sure you are always up to date on the latest adversarial groups and their TTPs. No more spreadsheets. No more guesswork. Only qualitative data and evidence-based decision making.
Why Interpres?
Interpres provides CTEM with the intelligence layer that unifies your security stack into a holistic and orchestrated solution with unbiased, evidence-based and continuous validation. Defense Surface Management is the foundation of CTEM.
To learn more about how Interpres Security can unify your CTEM program, read the whitepaper “Defense Surface Management: The Foundation Required to Properly Implement a Continuous Threat Exposure Management Program”. The whitepaper outlines how organizations can use DSM to prioritize and optimize their defenses and reduce threat exposure in a manner that is both efficient and effective. Get your copy here.