Recently, the U.S. and International Agencies release a Joint Cybersecurity Advisory (JCA) (People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection | CISA) regarding VOLT Typhoon “living off the land.” In other words, using built in network tools to evade detection. This report is significant because it highlights the need for a Continuous Threat Exposure Management (CTEM) system fueled by Intelligence to drive prioritization and remediation across a company’s enterprise.
Key Takeaways
The technical details list how VOLT Typhoon is targeting small office/home office (SOHO) remote worker’s infrastructure to establish a foothold that can then be used to target the parent network. Mitigations are listed to include what processes to monitor, what event ID’s to log, and best practices to follow. However, the mitigations are based on Cross-Sector Cybersecurity Performance Goals and are not tailored to a SMB organizations’ security stack or threat profile. Understanding the prioritization of the mitigation within the current workload will be difficult at best.
Interpres Resources

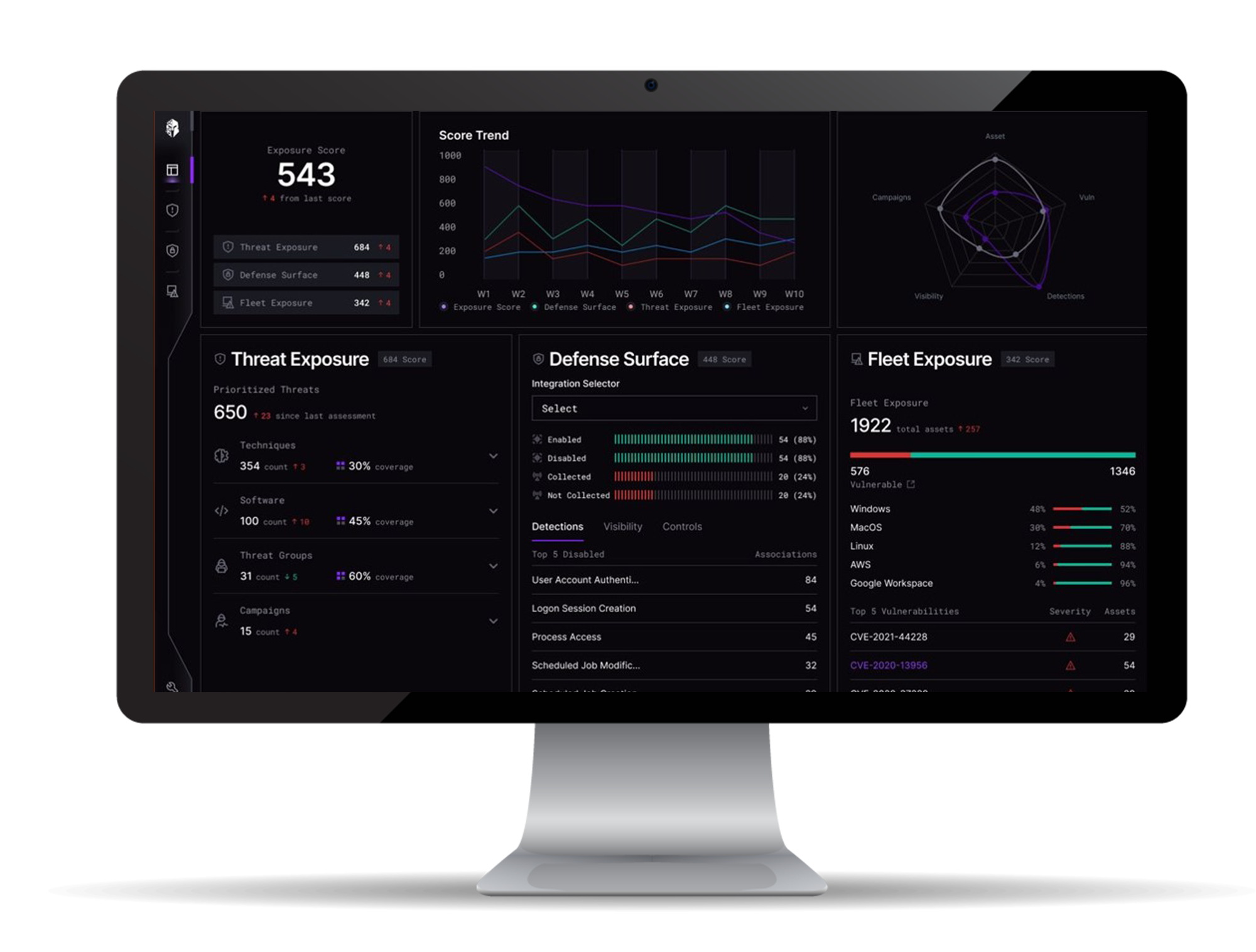
Interpres Security automatically ingests all JCAs and performs an automated “readiness” assessment tailored to your organization’s defensive capabilities. Interpres extracts all adversarial Tactics, Techniques, and Procedures (TTPs) detailed in the JCA and measures the risk exposure your organization has with regard to the identified campaign. Once TTPs have been extracted, Interpres analyzes your defensive toolsets, controls, and security logs to determine your organization’s readiness to defend against the identified TTPs. Interpres also measures fleet exposure by identifying assets present within the defended environment and prioritizing CVE patching efforts. Interpres allows for instant and continuous understanding of your organization’s risk exposure to adversarial campaigns while providing a prioritized mitigation path that is specific to your organization’s specific defensive capabilities.